Infection Monkey v1.10.0
This release introduces exciting new features, performance improvements, and lots of bug fixes. To start downloading it while you read the release notes, go to the Infection Monkey website.
New Features 🆕
New exploits 💣
Infection Monkey can now exploit two new remote code execution vulnerabilities:
- Exploit CVE-2019-6340 in Drupal #669
- Exploit Zerologon CVE-2020-1472 in Windows domain controllers #846, #868, #998, #1004
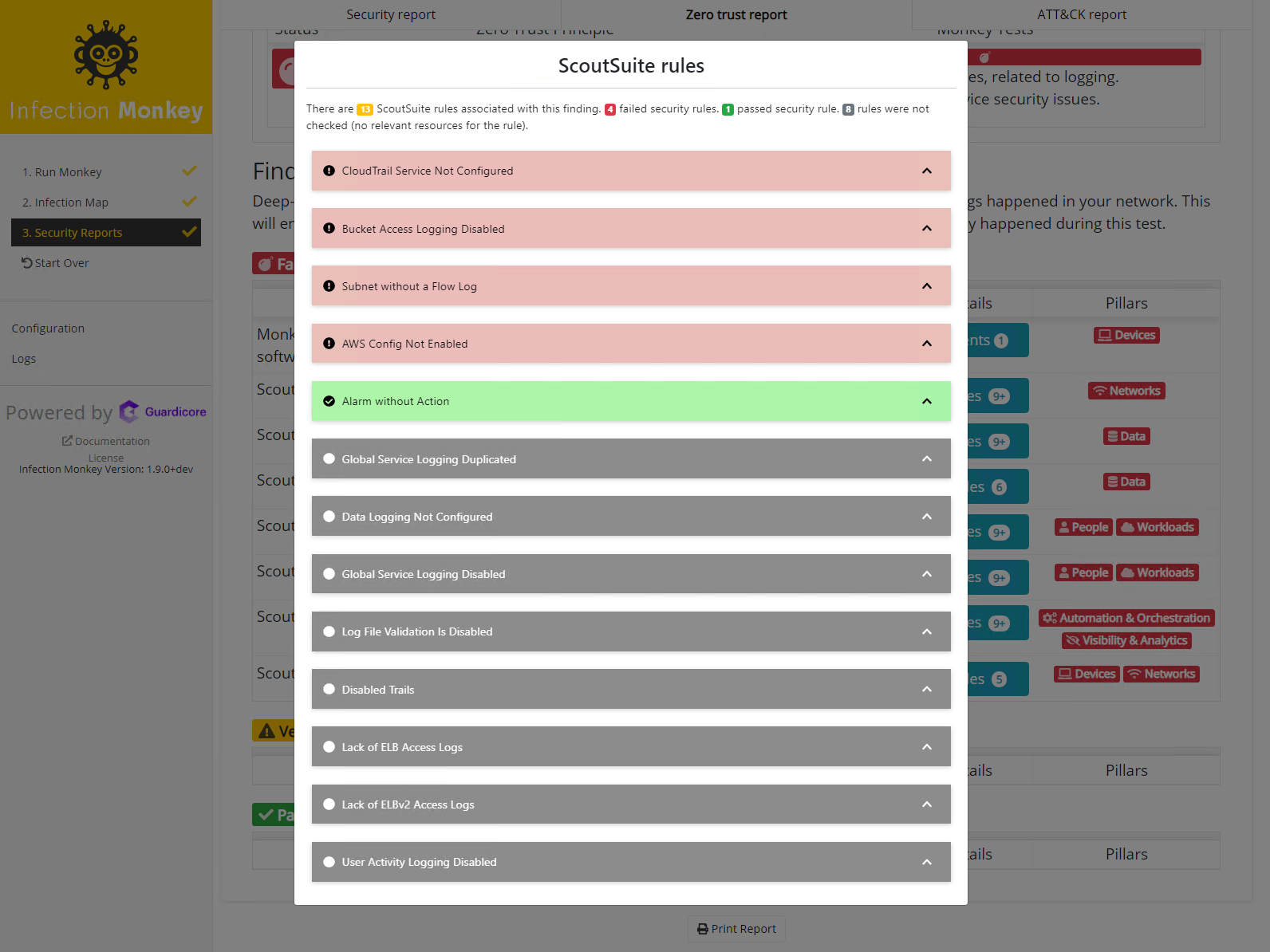
AWS Zero Trust security scans with ScoutSuite 🔍
Scout Suite is an open-source cloud security-auditing tool. It queries the cloud API to gather configuration data. Based on the configuration data gathered, ScoutSuite shows security issues and risks present in your cloud infrastructure. Infection Monkey will run a ScoutSuite scan against your AWS environment and categorize any alerts according to the Zero Trust framework. #519
New MITRE ATT&CK techniques 💥
We're continuing to improve our MITRE ATT&CK capabilities. We've added four new ATT&CK techniques to Infection Monkey, for a total of 36!
- Signed script proxy execution (T1216) #776
- Account discovery(T1087) #793
- Indicator removal on host: timestomp (T1099) #796
- Clear command history (T1146) #799
Improvements ⤴
Secured dependencies using snyk.io
Performance improvements 🚤
- Use multithreading to run PBAs #696
- Refactor tornado WSGE container into gevent WSGI container #858 #862
- Add sane timeouts to reduce excessive blocking #885
Documentation improvements 📖
We've updated our documentation for readability and consistency, as well as added swimm tutorials for developers.
- Improve report documentation #887
- Updates to monkey zoo docs #927
- Copyediting #909 #932 #933 #934 #935 #936 #937 #965
- Swimm tutorials #766 #837 #850 #904
- Add high-level architecture explanation #1047
Miscellaneous
- Add Windows XP support to MS08_067 exploit #809
- Reintroduce AWS run option #865
- Update Linux deployment scripts #900
UI
- Specify a user that will run the infection monkey agent #792 #830 #838 #840
- Clarified cross-segment issue reporting #819
- Improve ATT&CK UI #820
- Modify master checkboxes to conform to human interface guidelines #920
- Provide warning icon and language for unsafe options #920
- Show "None" in zero trust report sections with zero findings #947
- Show confirmation dialog when unsafe config is submitted or imported #1000
- Show warning dialog when unsafe ATT&CK config is submitted #1006
- Clarify custom PBA field descriptions in configuration menu #1027
Bug fixes 🐛
- Scale Monkey Island map component to window size #150
- Center Guardicore logo on smaller screens #612
- Fix typo that caused missing telemetry type on Log page #689
- Redirect to login page when JWT expires #739
- Link related ATT&CK techniques of the same PBA #761
- Fix rendering in security report generation #762
- Fix PBA file upload failure #784
- Evade detection by Windows defender #801, #929
- Fix hang on update check #857
- Fix creation of scheduled jobs (PBA) #861
- Fix wrong initial state in plugin selector control #891
- Fix failing SMB exploiter #895
- Catch exceptions thrown by fingerprinters #897
- Fix logic used to detect AWS, GCP, and Azure cloud instances #902
- Fix uncaught error in ATT&CK report #948
- Fix failure to scan configured TCP ports #956
- Add missing authentication check to
local_runendpoint #981 - Do not automatically execute custom PBA script #1020 #1027
- Fix pyjwt dependency at version 1.7 #1042
- Properly handle unicode decode errors #798
New contributors 🙌
Welcome and thanks to our new contributors:
Attached binaries and hashes:
| Filename | Type | Version | SHA256 Hash |
|---|---|---|---|
| monkey-linux-32 | agent | 1.10.0 | a6de7d571051292b9db966afe025413dc20b214c4aab53e48d90d8e04264f4f5 |
| monkey-linux-64 | agent | 1.10.0 | 932f703510b6484c3824fc797f90f99722e38a7f8956cf6fa58fdecb3790ab93 |
| monkey-windows-32 | agent | 1.10.0 | 8e891e90b11b97fbbef27f1408c1fcad486b19c612773f2d6a9edac5d4cdb47f |
| monkey-windows-64 | agent | 1.10.0 | 3b499a4cf1a67a33a91c73b05884e4d6749e990e444fa1d2a3281af4db833fa1 |
| sc_monkey_runner32.so | sambacry | 68fd441c92f9d2c3201f7072eafbe9a4c56339139395daeba959836bd3f8b212 | |
| sc_monkey_runner64.so | sambacry | 94e1d1ac64bfc4a63f590f8add21c10f26b2b0ffb6b69518ed2c53909c8faf18 | |
| tracerouter32 | traceroute | c15a8a7612af31ff973d424c6473eb34e2ca66dddc6aef3067a1e9927e368f23 | |
| traceroute64 | sambacry | 64d5c9c9b7c0aaf6447bd6fd439b87052fe72bba769c4de454bc1f817cffcad4 |