-
Notifications
You must be signed in to change notification settings - Fork 160
AppControl Manager
AppControl Manager is a modern secure app that provides easy to use graphical user interface to manage App Control and Code Integrity on your device.
The short-term goal is for the AppControl manager to reach feature parity with the WDACConfig Powershell module, as fast as possible, and then to surpass it with new unique features and improvements.
Important
The AppControl Manager application is built publicly using a GitHub action and uploaded to the GitHub release. The action uses Artifact Attestation and SBOM (Software Bill of Materials) generation to comply with SLSA level 2 and security standards. The source code as well as the package is uploaded to Virus Total automatically. Also GitHub's CodeQL Advanced workflow with extended security model scans the entire repository.
What is App Control for business? check out this article
Use the following PowerShell command as Admin, it will automatically download the latest MSIX file from this repository's release page and install it for you.
(irm 'https://raw.githubusercontent.com/HotCakeX/Harden-Windows-Security/main/Harden-Windows-Security.ps1')+'AppControl'|iexPlease feel free to open a discussion if you have any questions about the build process, security, how to use or have feedbacks. Source code on this repository
- Windows 11 24H2
- Windows 11 23H2
- Windows 11 22H2
- Windows Server 2025
- Secure and transparent development and build process.
- Built using WinUI3 / XAML / C#.
- Built using the latest .NET.
- Powered by the WinAppSDK (formerly Project Reunion).
- Packaged with the modern MSIX format.
- Incorporates the Mica material design for backgrounds.
- Adopts the Windows 11 Fluent design system.
- Fast execution and startup time.
- 0 required dependency.
- 0 Third-party library or file used.
- 0 Telemetry or data collection.
- 0 Windows Registry changes.
- 100% clean uninstallation.
- 100% open-source and free to use.
-
 Create AppControl Policy
Create AppControl Policy
-
 Create Supplemental Policy
Create Supplemental Policy
-
 System Information
System Information
-
 Configure Policy Rule Options
Configure Policy Rule Options
-
 Simulation
Simulation
-
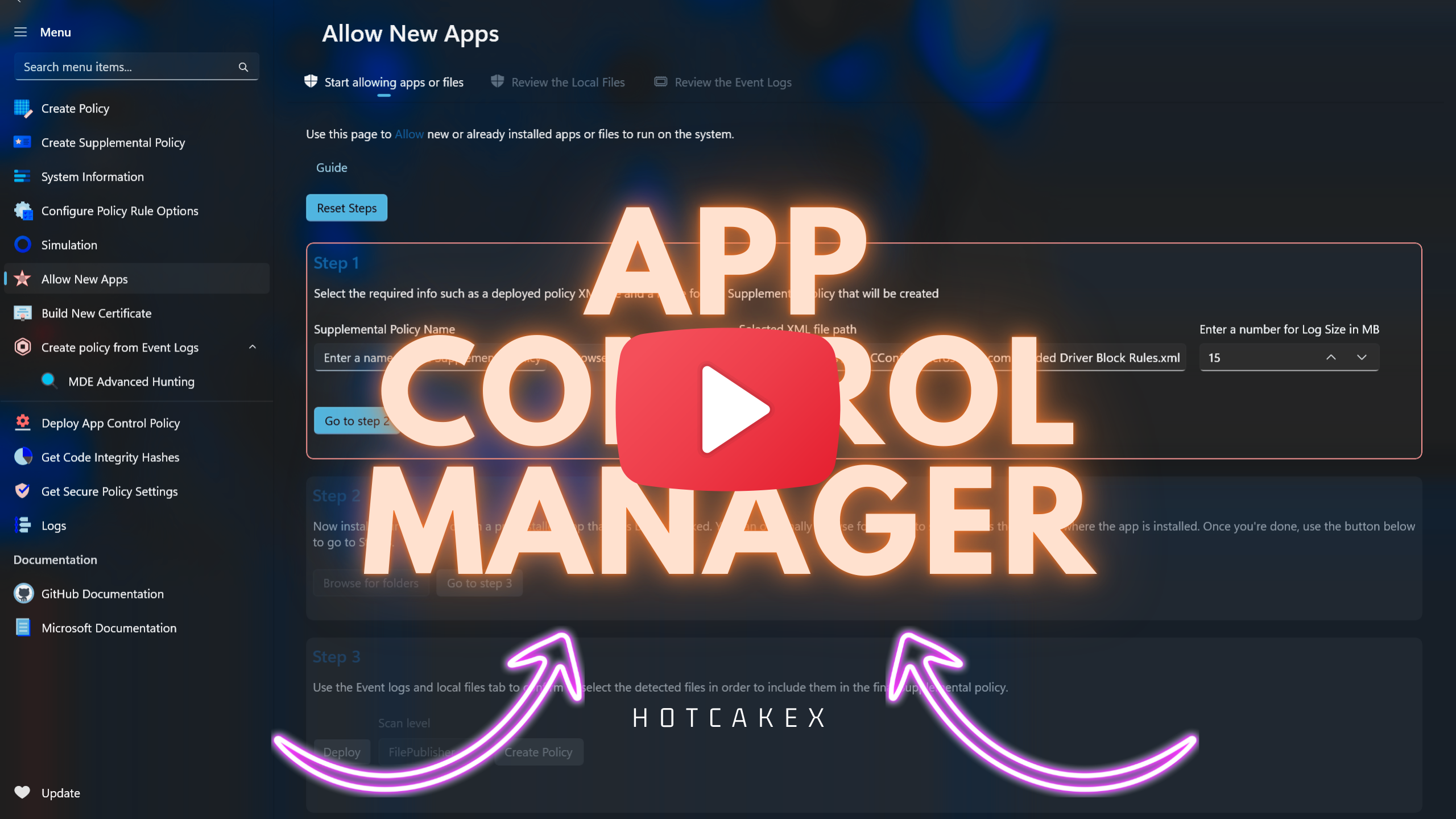
 Allow New Apps
Allow New Apps
-
 Build New Certificate
Build New Certificate
-
 Create Policy From Event Logs
Create Policy From Event Logs
-
 Create Policy From MDE Advanced Hunting
Create Policy From MDE Advanced Hunting
-
 Merge App Control Policies
Merge App Control Policies
-
 Deploy App Control Policy
Deploy App Control Policy
-
 Get Code Integrity Hashes
Get Code Integrity Hashes
-
 Get Secure Policy Settings
Get Secure Policy Settings
-
 Update
Update
More features will come very quickly in the near future.
Security is paramount when selecting any application designed to safeguard your systems. The last thing you want is a security-focused tool that inadvertently expands your attack surface or one that doesn't prioritize security at its core.
AppControl Manager is engineered with a security-first approach from the ground up. It's crafted specifically for defense teams, yet its design has been rigorously shaped with a keen awareness of potential offensive strategies, ensuring resilience against emerging threats.
-
The AppControl Manager does not rely on any 3rd party component or dependency. All the logics are built securely and specifically for the app.
-
Any file(s) the AppControl Manager ever produces, uses or expects is only from an Administrator-protected location in
C:\Program Files\WDACConfig. -
The AppControl Manager supports process mitigations / Exploit Protections such as:
Blocking low integrity images,Blocking remote images,Blocking untrusted fonts,Disabling extension points,Export Address Filtering,Hardware enforced stack protection,Import Address Filtering,Validate handle usage,Validate stack integrityand so on. -
The AppControl Manager always uses the latest .NET and SDK versions, ensuring all the security patches released by Microsoft will be included.
-
The entire codebase is thoroughly commented, allowing code reviewers to effortlessly examine and verify every aspect of AppControl Manager's source code.
-
AppControl Manager operates exclusively within the "WDACConfig" directory located in the
Program Filesdirectory for all read and write operations. No data is accessed or modified outside this directory. This design ensures that non-elevated processes, unauthorized software, or unprivileged malware on the system cannot alter the policies you create, the certificates you generate, or the CIP binary files you deploy. -
Administrator privileges are required for scanning Code Integrity and AppLocker logs. These scans are integral to several application functions, providing enhanced insights and enabling the generation of precise supplemental policies tailored to your needs.
-
Deploying, removing, modifying, or checking the status of policies also necessitates Administrator privileges to ensure secure and reliable execution of these operations.
The installation process for AppControl Manager is uniquely streamlined. When you execute the PowerShell one-liner command mentioned above, it initiates a file containing the AppControl function, which serves as the bootstrapper script. This script is thoroughly documented, with detailed explanations and justifications for each step, as outlined below:
-
The latest version of the AppControl Manager MSIX package is securely downloaded from the GitHub release page, where it is built publicly with full artifact attestation and SBOMs.
-
The
SignTool.exeutility is sourced directly from Microsoft by retrieving the associated Nuget package, ensuring a trusted origin. -
A secure, on-device code-signing certificate is then generated. This certificate, managed by the Microsoft-signed
SignTool.exe, is used to sign the MSIX package obtained from GitHub. -
The private key of the certificate is non-exportable, never written on the disk and is securely discarded once signing is complete, leaving only the public key on the device to allow AppControl Manager to function properly on the system and prevent the certificate from being able to sign anything else.
-
The entire process is designed to leave no residual files. Each time the script runs, any certificates from previous executions are detected and removed, ensuring a clean system.
-
Finally, the
AppControlManager.dllandAppControlManager.exefiles are added to the Attack Surface Reduction (ASR) exclusions to prevent ASR rules from blocking these newly released binaries. Previous version exclusions are also removed from the ASRs exclusions list to maintain a clean, streamlined setup for the user.
Here is the complete list of all of the URLs the AppControl Manager application connects to (or is mentioned in the User Interface) with proper justification for each of them.
| URL | Justification |
|---|---|
| https://api.nuget.org/v3-flatcontainer/ | To access Microsoft NuGet repository to download SignTool.exe |
| https://aka.ms/VulnerableDriverBlockList | To download the Microsoft Recommended Drivers Block List |
| https://api.github.com/repos/MicrosoftDocs/windows-itpro-docs/commits | To check the latest commit details of the Microsoft Recommended Drivers Block List and display them to the user on the UI |
| https://raw.githubusercontent.com/MicrosoftDocs/windows-itpro-docs/refs/heads/public/windows/security/application-security/application-control/app-control-for-business/design/applications-that-can-bypass-appcontrol.md | Source for the Microsoft Recommended User-Mode Block Rules |
| https://raw.githubusercontent.com/MicrosoftDocs/windows-itpro-docs/refs/heads/public/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules.md | Source for the Microsoft Recommended Drivers Block Rules |
| https://raw.githubusercontent.com/HotCakeX/Harden-Windows-Security/refs/heads/main/AppControl%20Manager/DownloadURL.txt | The file on this repository that contains the download link to the latest version of the AppControl Manager. That text file is updated via automated GitHub action workflow that securely builds and uploads the MSIX package to the GitHub releases. |
| https://raw.githubusercontent.com/HotCakeX/Harden-Windows-Security/refs/heads/main/AppControl%20Manager/version.txt | The latest available version of the AppControl Manager application. That text file is updated via automated GitHub action workflow that securely builds and uploads the MSIX package to the GitHub releases. |
| https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction | The link that opens in the GitHub documentations page in the app via the built-in WebView 2 |
| https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/appcontrol | The link that opens in the Microsoft documentations page in the app via the built-in WebView 2 |
| https://github.com/HotCakeX/Harden-Windows-Security/issues/415 | A link to one of the GitHub issues |
| https://github.com/HotCakeX/Harden-Windows-Security/releases | During the update process, this link that is for the GitHub releases will be displayed on the update page as a quick way to read the release notes |
| https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager | Will be displayed on the Update page when a new version is available and being downloaded |
| https://github.com/HotCakeX/Harden-Windows-Security/issues/new/choose | Link for the "Send Feedback" button at the bottom of the about section in settings |
| https://github.com/HotCakeX/Harden-Windows-Security | Mentioned in the Links section at the bottom of the About section in Settings |
| https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager | Mentioned in the Links section at the bottom of the About section in Settings |
| https://spynetgirl.github.io/ | Mentioned in the Links section at the bottom of the About section in Settings |
| https://www.youtube.com/@hotcakex | Mentioned in the Links section at the bottom of the About section in Settings |
| https://x.com/CyberCakeX | Mentioned in the Links section at the bottom of the About section in Settings |
| https://icons8.com | Mentioned in the Links section at the bottom of the About section in Settings as credit |
-
Download this PowerShell script.
-
Have
SignTool.exe. You can find it in here if you don't already have it. -
Download the latest MSIX package of the AppControl Manager from the GitHub releases or build it from the source code yourself.
-
Start an elevated PowerShell and import the script file via
Import-Module "Path to script file". -
Use the following syntax to Install the AppControl Manager
AppControl -MSIXPath "Path To the MSIX" -SignTool "Path to signtool.exe" -Verbose- Q: Why isn't AppControl Manager on Microsoft Store?
- A: Because Microsoft Store currently does not accept apps that require Administrator privileges to run (i.e., MediumIL).
- Q: Why isn't the MSIX package pre-signed?
- A: Because I haven't started paying for a code-signing certificate yet.
- Create AppControl Policy
- Create Supplemental Policy
- System Information
- Configure Policy Rule Options
- Simulation
- Allow New Apps
- Build New Certificate
- Create Policy From Event Logs
- Create Policy From MDE Advanced Hunting
- Merge App Control Policies
- Deploy App Control Policy
- Get Code Integrity Hashes
- Get Secure Policy Settings
- Update
- Introduction
- App Control for Lightly Managed Devices
- App Control for Fully managed device - Variant 1
- App Control for Fully managed device - Variant 2
- App Control for Fully managed device - Variant 3
- App Control for Fully managed device - Variant 4
- App Control Notes
- How to Create and Deploy a Signed App Control Policy
- Fast and Automatic Microsoft Recommended Driver Block Rules updates
- App Control policy for BYOVD Kernel mode only protection
- EKUs in App Control for Business Policies
- App Control Rule Levels Comparison and Guide
- Script Enforcement and PowerShell Constrained Language Mode in App Control Policies
- How to Use Microsoft Defender for Endpoint Advanced Hunting With App Control
- App Control Frequently Asked Questions (FAQs)
- New-WDACConfig
- New-SupplementalWDACConfig
- Remove-WDACConfig
- Edit-WDACConfig
- Edit-SignedWDACConfig
- Deploy-SignedWDACConfig
- Confirm-WDACConfig
- New-DenyWDACConfig
- Set-CommonWDACConfig
- New-KernelModeWDACConfig
- Get-CommonWDACConfig
- Remove-CommonWDACConfig
- Assert-WDACConfigIntegrity
- Test-CiPolicy
- Get-CiFileHashes
- Get-CIPolicySetting
- Create Bootable USB flash drive with no 3rd party tools
- Event Viewer
- Group Policy
- How to compact your OS and free up extra space
- Hyper V
- Overrides for Microsoft Security Baseline
- Git GitHub Desktop and Mandatory ASLR
- Signed and Verified commits with GitHub desktop
- About TLS, DNS, Encryption and OPSEC concepts
- Things to do when clean installing Windows
- Comparison of security benchmarks
- BitLocker, TPM and Pluton | What Are They and How Do They Work
- How to Detect Changes in User and Local Machine Certificate Stores in Real Time Using PowerShell
- Cloning Personal and Enterprise Repositories Using GitHub Desktop
- Only a Small Portion of The Windows OS Security Apparatus
- Rethinking Trust: Advanced Security Measures for High‐Stakes Systems
- Clean Source principle, Azure and Privileged Access Workstations
- How to Securely Connect to Azure VMs and Use RDP
- Basic PowerShell tricks and notes
- Basic PowerShell tricks and notes Part 2
- Basic PowerShell tricks and notes Part 3
- Basic PowerShell tricks and notes Part 4
- Basic PowerShell tricks and notes Part 5
- How To Access All Stream Outputs From Thread Jobs In PowerShell In Real Time
- PowerShell Best Practices To Follow When Coding
- How To Asynchronously Access All Stream Outputs From Background Jobs In PowerShell
- Powershell Dynamic Parameters and How to Add Them to the Get‐Help Syntax
- RunSpaces In PowerShell
- How To Use Reflection And Prevent Using Internal & Private C# Methods in PowerShell