-
Notifications
You must be signed in to change notification settings - Fork 77
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Update libs dependency #2775
base: main
Are you sure you want to change the base?
Update libs dependency #2775
Conversation
Deploying vald with
|
| Latest commit: |
b9a4264
|
| Status: | ✅ Deploy successful! |
| Preview URL: | https://e5e2d62d.vald.pages.dev |
| Branch Preview URL: | https://create-pull-request-patch.vald.pages.dev |
|
Warning There were issues while running some tools. Please review the errors and either fix the tool’s configuration or disable the tool if it’s a critical failure. 🔧 golangci-lint (1.62.2)level=warning msg="[config_reader] The configuration option 📝 Walkthrough📝 WalkthroughWalkthroughThis pull request involves a comprehensive update of version numbers across multiple files in the Vald project. The changes primarily focus on updating the Kubernetes version from Changes
Suggested labels
Suggested reviewers
Possibly related PRs
📜 Recent review detailsConfiguration used: CodeRabbit UI 📒 Files selected for processing (1)
🚧 Files skipped from review as they are similar to previous changes (1)
Thank you for using CodeRabbit. We offer it for free to the OSS community and would appreciate your support in helping us grow. If you find it useful, would you consider giving us a shout-out on your favorite social media? 🪧 TipsChatThere are 3 ways to chat with CodeRabbit:
Note: Be mindful of the bot's finite context window. It's strongly recommended to break down tasks such as reading entire modules into smaller chunks. For a focused discussion, use review comments to chat about specific files and their changes, instead of using the PR comments. CodeRabbit Commands (Invoked using PR comments)
Other keywords and placeholders
CodeRabbit Configuration File (
|
|
[CHATOPS:HELP] ChatOps commands.
|
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 0
🧹 Outside diff range and nitpick comments (4)
charts/vald/values.schema.json (1)
3720-3720: Consider consistent formatting for enum valuesSome locations use single-line format while others use multi-line format for the same enum values. Consider standardizing the format across all locations for better maintainability.
Also applies to: 7419-7419, 12240-12240, 15013-15013
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (3)
Line range hint
199-212: Consider additional TLS certificate validationWhile the TLS configuration structure is correct, consider adding pattern validation for certificate paths and additional validation for when TLS is enabled.
tls: properties: ca: type: string + pattern: ^(/[-\w\d.]+)+\.(?:crt|pem)$ cert: type: string + pattern: ^(/[-\w\d.]+)+\.(?:crt|pem)$ enabled: type: boolean insecure_skip_verify: type: boolean key: type: string + pattern: ^(/[-\w\d.]+)+\.(?:key|pem)$ + required: + - enabled + allOf: + - if: + properties: + enabled: + enum: [true] + then: + required: [ca, cert, key] type: object
Line range hint
356-378: Consider adding duration format validationWhile the search configuration is comprehensive, consider adding pattern validation for the timeout field to ensure it follows the Go duration format (e.g., "1h", "30m", "30s").
timeout: type: string + pattern: ^([0-9]+h)?([0-9]+m)?([0-9]+s)?$
Line range hint
603-786: Consider additional validation for server configurationsThe gRPC and REST server configurations are comprehensive, but consider adding validation for timing-related fields to ensure they follow the proper duration format.
connection_timeout: type: string + pattern: ^([0-9]+h)?([0-9]+m)?([0-9]+s)?$ max_conn_age: type: string + pattern: ^([0-9]+h)?([0-9]+m)?([0-9]+s)?$ handler_timeout: type: string + pattern: ^([0-9]+h)?([0-9]+m)?([0-9]+s)?$
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
⛔ Files ignored due to path filters (4)
apis/grpc/v1/agent/sidecar/sidecar_vtproto.pb.gois excluded by!**/*.pb.go,!**/*.pb.goexample/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (11)
.github/ISSUE_TEMPLATE/bug_report.md(1 hunks).github/ISSUE_TEMPLATE/security_issue_report.md(1 hunks).github/PULL_REQUEST_TEMPLATE.md(1 hunks)charts/vald-benchmark-operator/values.schema.json(2 hunks)charts/vald/values.schema.json(17 hunks)example/client/go.mod(1 hunks)go.mod(3 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml(1 hunks)versions/KUBECTL_VERSION(1 hunks)
✅ Files skipped from review due to trivial changes (6)
- .github/ISSUE_TEMPLATE/security_issue_report.md
- .github/ISSUE_TEMPLATE/bug_report.md
- .github/PULL_REQUEST_TEMPLATE.md
- example/client/go.mod
- versions/KUBECTL_VERSION
- go.mod
🔇 Additional comments (12)
charts/vald/values.schema.json (1)
3720-3720: Verify the MetricInterceptor implementation and existing configurations
The schema changes consistently add "MetricInterceptor" as a valid option across all gRPC client interceptor definitions. While the change itself is well-structured, we should verify a few things:
- The implementation of MetricInterceptor exists and is ready for use
- The impact on existing configurations that may need to be updated
Let's verify the implementation and usage:
Also applies to: 7056-7059, 7419-7419, 7771-7774, 9651-9654, 10002-10005, 10354-10357, 12240-12240, 14296-14299, 14647-14650, 15013-15013, 16708-16711, 17059-17062, 18760-18763, 19111-19114, 22491-22494, 22842-22845
✅ Verification successful
MetricInterceptor implementation is verified and properly integrated
The implementation of MetricInterceptor is confirmed to exist in the codebase with both server and client implementations:
- Server:
internal/net/grpc/interceptor/server/metric/metric.go - Client:
internal/net/grpc/interceptor/client/metric/metric.go
The interceptor is properly integrated into the gRPC server and client options:
- Server integration:
internal/servers/server/option.go - Client integration:
internal/net/grpc/option.go
The schema changes are consistent with the existing implementation and current usage in configuration files.
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Check for MetricInterceptor implementation
echo "Searching for MetricInterceptor implementation..."
rg -t go "type MetricInterceptor" -l
# Check for existing usage in configurations
echo "Checking existing configurations..."
rg -t yaml "interceptors:" -A 5 "charts/"
Length of output: 29496
Script:
#!/bin/bash
# Let's search for the MetricInterceptor implementation in Go files
echo "Searching for MetricInterceptor implementation and usage..."
rg -t go "MetricInterceptor" -A 5
# Also check for any recent changes related to MetricInterceptor
echo "Checking recent changes..."
git log -n 5 --oneline --grep="MetricInterceptor"
Length of output: 4420
k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml (4)
69-72: LGTM: Improved type constraints for dataset properties.
The explicit type definitions and constraints for group and indexes properties enhance schema validation.
97-102: LGTM: Enhanced type definitions for dataset and jobs.
The explicit type definitions for dataset and jobs properties improve schema clarity.
107-115: LGTM: Improved target configuration constraints.
The addition of constraints for host and port properties enhances validation:
hostrequires minimum length of 1portis properly bounded between 0 and 65535
77-89: Consider removing the enum constraint for the dataset name.
The name property's enum constraint has been removed, making it more flexible. However, ensure this change is intentional and won't break existing implementations that rely on specific dataset names.
k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml (2)
167-170: LGTM: Enhanced gRPC client interceptor configuration.
Added support for MetricInterceptor alongside TraceInterceptor in the client configuration.
704-712: LGTM: Comprehensive gRPC server interceptor configuration.
Added support for multiple interceptors with clear enumeration:
- RecoverInterceptor
- AccessLogInterceptor
- TraceInterceptor
- MetricInterceptor
charts/vald-benchmark-operator/values.schema.json (1)
167-170: LGTM: Consistent schema definitions with CRD.
The values schema correctly mirrors the CRD changes for interceptor configurations:
- Client interceptors:
TraceInterceptor,MetricInterceptor - Server interceptors:
RecoverInterceptor,AccessLogInterceptor,TraceInterceptor,MetricInterceptor
Also applies to: 704-712
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (4)
141-144: LGTM: Interceptors configuration enhanced
The addition of MetricInterceptor to the allowed interceptors aligns with the gRPC client interceptor updates mentioned in the PR summary.
248-281: LGTM: Comprehensive dataset validation
The dataset configuration includes:
- Proper validation for group names (minLength: 1)
- Valid range checks for indexes
- Enum validation for dataset names
- Required field validation
Line range hint 379-602: LGTM: Well-structured health check configurations
The health check configurations (liveness, readiness, startup) follow Kubernetes best practices with:
- Proper port range validation
- Complete probe configurations
- Appropriate HTTP endpoint settings
Line range hint 1-823: LGTM: Well-structured and comprehensive CRD schema
The CRD schema is well-defined with:
- Proper type definitions for all fields
- Comprehensive validation rules
- Appropriate constraints for numeric values
- Clear enum definitions
- Required field specifications
The changes align with the PR objective of updating dependencies and follow Kubernetes best practices.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 1
🧹 Outside diff range and nitpick comments (3)
charts/vald/values.schema.json (1)
3720-3720: Consider consistent array formattingThe enum arrays use inconsistent formatting across different locations:
- Single-line format:
["TraceInterceptor", "MetricInterceptor"]- Multi-line format with indentation
While both are valid JSON, maintaining consistent formatting would improve readability.
Consider using the multi-line format consistently across all locations:
- "enum": ["TraceInterceptor", "MetricInterceptor"] + "enum": [ + "TraceInterceptor", + "MetricInterceptor" + ]Also applies to: 7056-7059, 7419-7419, 7771-7774, 9651-9654, 10002-10005, 10354-10357, 12240-12240, 14296-14299, 14647-14650, 15013-15013, 16708-16711, 17059-17062, 18760-18763, 19111-19114, 22491-22494, 22842-22845
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (2)
281-309: Consider adding default values for logging configurationWhile the schema structure is good, consider adding default values for:
- logging.format (e.g., default: "json")
- logging.level (e.g., default: "info")
- logging.logger (e.g., default: "zap")
Line range hint
602-786: Server configuration structure is well-definedThe server configuration schema:
- Properly validates port numbers
- Includes comprehensive health check configurations
- Provides detailed gRPC and REST server options
However, consider adding validation for the probe timing values:
probe_wait_time: type: string + pattern: ^([0-9]+h)?([0-9]+m)?([0-9]+s)?([0-9]+ms)?([0-9]+us)?([0-9]+ns)?$
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
⛔ Files ignored due to path filters (4)
apis/grpc/v1/agent/sidecar/sidecar_vtproto.pb.gois excluded by!**/*.pb.go,!**/*.pb.goexample/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (11)
.github/ISSUE_TEMPLATE/bug_report.md(1 hunks).github/ISSUE_TEMPLATE/security_issue_report.md(1 hunks).github/PULL_REQUEST_TEMPLATE.md(1 hunks)charts/vald-benchmark-operator/values.schema.json(2 hunks)charts/vald/values.schema.json(17 hunks)example/client/go.mod(1 hunks)go.mod(3 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml(1 hunks)versions/KUBECTL_VERSION(1 hunks)
✅ Files skipped from review due to trivial changes (5)
- .github/ISSUE_TEMPLATE/bug_report.md
- .github/ISSUE_TEMPLATE/security_issue_report.md
- versions/KUBECTL_VERSION
- .github/PULL_REQUEST_TEMPLATE.md
- example/client/go.mod
🔇 Additional comments (15)
go.mod (3)
Line range hint 1-1: LGTM - Routine dependency updates
The dependency updates are minor version or patch version changes, suggesting routine maintenance and bug fixes. The verification scripts will help confirm there are no breaking changes or security implications.
134-134: Verify go-json update compatibility
The update from v0.10.3 to v0.10.4 is a patch version change for this critical JSON handling library.
✅ Verification successful
Update to go-json v0.10.4 is safe to proceed
The patch update includes two bug fixes:
- Fixed handling of
[]*time.Timenil checks - Improved initialization in decoder/encoder with lazy loading
No security vulnerabilities or breaking changes were found. The changes are minor optimizations that enhance reliability.
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check changelog and release notes for breaking changes
# Check the release notes
gh api repos/goccy/go-json/releases/tags/v0.10.4 --jq '.body'
# Check for any security advisories
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "github.com/goccy/go-json") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
Length of output: 925
39-39: Verify cloudsql-proxy update compatibility
The update from v1.37.2 to v1.37.3 is a patch version change.
✅ Verification successful
✅ Safe to update cloudsql-proxy to v1.37.3
The update from v1.37.2 to v1.37.3 is a safe patch version change that only includes dependency updates. The release notes show:
- Only contains bug fixes (dependency bumps)
- No breaking changes
- No security vulnerabilities reported
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check changelog and release notes for breaking changes
# Check the release notes
gh api repos/GoogleCloudPlatform/cloudsql-proxy/releases/tags/v1.37.3 --jq '.body'
# Check for any security advisories
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "github.com/GoogleCloudPlatform/cloudsql-proxy") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
Length of output: 2145
charts/vald/values.schema.json (2)
3720-3720: Verify impact on existing configurations
The addition of "MetricInterceptor" to the enum should be backward compatible, but let's verify existing configurations won't be affected.
Also applies to: 7056-7059, 7419-7419, 7771-7774, 9651-9654, 10002-10005, 10354-10357, 12240-12240, 14296-14299, 14647-14650, 15013-15013, 16708-16711, 17059-17062, 18760-18763, 19111-19114, 22491-22494, 22842-22845
✅ Verification successful
Based on the search results, I can generate the final response since I have enough information to verify the impact of adding "MetricInterceptor" to the enum:
Adding MetricInterceptor is backward compatible with existing configurations
The search results show that existing configurations primarily use "TraceInterceptor" and "RecoverInterceptor" in their interceptor lists. The addition of "MetricInterceptor" as a new enum option:
- Does not modify any existing interceptor configurations
- Maintains compatibility with current values since it's an additive change to the enum
- Preserves the functionality of existing interceptors like TraceInterceptor
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Search for existing interceptor configurations in Helm values files
echo "Searching for existing interceptor configurations..."
fd -e yaml -e values.yaml | xargs rg "interceptors:"
# Search for TraceInterceptor usage in values files
echo "Searching for TraceInterceptor usage..."
fd -e yaml -e values.yaml | xargs rg "TraceInterceptor"
Length of output: 56758
3720-3720: Verify the MetricInterceptor implementation
The schema now includes "MetricInterceptor" alongside "TraceInterceptor" across all gRPC client interceptor configurations. Let's verify the implementation exists.
Also applies to: 7056-7059, 7419-7419, 7771-7774, 9651-9654, 10002-10005, 10354-10357, 12240-12240, 14296-14299, 14647-14650, 15013-15013, 16708-16711, 17059-17062, 18760-18763, 19111-19114, 22491-22494, 22842-22845
✅ Verification successful
Based on the search results, I can see that the MetricInterceptor implementation exists in the codebase:
- Client-side implementation:
internal/net/grpc/interceptor/client/metric/metric.goprovidesClientMetricInterceptors()- Used in
internal/net/grpc/option.goviametric.ClientMetricInterceptors()
- Server-side implementation:
internal/net/grpc/interceptor/server/metric/metric.goprovidesMetricInterceptors()- Used in
internal/servers/server/option.goviametric.MetricInterceptors()
Let me verify the actual interceptor implementations:
MetricInterceptor implementation verified
The MetricInterceptor is properly implemented in the codebase with both client and server-side implementations:
- Client: Creates latency histogram metrics for gRPC client calls
- Server: Creates latency histogram metrics for gRPC server requests
The schema changes are valid as they reflect the actual implementation in the codebase.
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Search for MetricInterceptor implementation
echo "Searching for MetricInterceptor implementation..."
rg -t go "type MetricInterceptor" -A 5
# Search for MetricInterceptor usage in Go files
echo "Searching for MetricInterceptor usage..."
rg -t go "MetricInterceptor"
# Search for related metrics configuration
echo "Searching for metrics configuration..."
fd -e yaml -e json | xargs rg "metrics?"
Length of output: 65977
Script:
#!/bin/bash
# Check metric interceptor implementations
echo "Checking client metric interceptor implementation..."
rg -t go -A 10 "func ClientMetricInterceptors" internal/net/grpc/interceptor/client/metric/
echo "Checking server metric interceptor implementation..."
rg -t go -A 10 "func MetricInterceptors" internal/net/grpc/interceptor/server/metric/
Length of output: 2415
k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml (3)
69-97: LGTM: Dataset schema improvements enhance validation.
The dataset property schema has been properly structured with:
- Explicit type definitions
- Appropriate minimum constraints for numeric fields
- Clear required field specifications
98-102: LGTM: Jobs array schema maintains flexibility.
The jobs array schema correctly:
- Defines items as objects
- Preserves unknown fields for extensibility
103-115: LGTM: Target schema properly constrains network configuration.
The target property schema appropriately:
- Enforces minimum length for host
- Constrains port within valid range (0-65535)
- Specifies required fields
k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml (1)
608-614: LGTM: gRPC interceptor types properly expanded.
The interceptors enum has been appropriately updated to include all required types:
- RecoverInterceptor
- AccessLogInterceptor
- TraceInterceptor
- MetricInterceptor
This aligns with the changes in values.schema.json.
charts/vald-benchmark-operator/values.schema.json (3)
167-170: LGTM: Client interceptor configuration properly updated.
The client interceptors enum correctly includes:
- TraceInterceptor
- MetricInterceptor
704-712: LGTM: Server interceptor configuration properly updated.
The server interceptors enum correctly includes all required types:
- RecoverInterceptor
- AccessLogInterceptor
- TraceInterceptor
- MetricInterceptor
167-170: Verify consistency of interceptor configurations across the codebase.
Let's ensure the interceptor configurations are consistent across all related files.
Also applies to: 704-712
✅ Verification successful
Let me search for more specific information about the schema and benchmark operator configurations.
Interceptor configurations are consistent across the codebase
The verification shows that the interceptor configurations in values.schema.json are consistent with other related files in the benchmark operator:
- The schema definitions correctly list
TraceInterceptorandMetricInterceptoras valid enum values - The CRDs (valdbenchmarkoperatorrelease.yaml, valdbenchmarkjob.yaml) and schema files maintain the same interceptor configurations
- The values.yaml and job-values.yaml schemas align with these definitions
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check consistency of interceptor configurations across the codebase
# Search for interceptor configurations in yaml and json files
echo "Checking interceptor configurations in yaml and json files..."
rg -U --type yaml --type json 'interceptors:(\s+|\n+)-.*Interceptor' -A 5
Length of output: 10730
Script:
#!/bin/bash
# Check schema definitions and benchmark operator configurations
echo "Checking schema and benchmark operator configurations..."
# Search for TraceInterceptor and MetricInterceptor in schema files
echo "=== Schema definitions ==="
rg -U --type json --type yaml "TraceInterceptor|MetricInterceptor" charts/vald-benchmark-operator/
# Search for benchmark scenario configurations
echo -e "\n=== Benchmark scenario configurations ==="
rg -U --type yaml "kind:\s+ValdbenchmarkScenario" -A 10
Length of output: 3059
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (3)
257-272: Dataset range validation looks good
The schema properly enforces:
- Valid dataset names (original, fashion-mnist)
- Required start and end range values
- Minimum value validation for indexes
Line range hint 1-823: Verify schema compatibility with existing configurations
The schema changes look comprehensive and well-structured. However, we should verify compatibility with existing ValdBenchmarkJob configurations.
✅ Verification successful
Based on the search results, I found three existing ValdBenchmarkJob configurations:
- charts/vald-benchmark-operator/crds/valdbenchmarkjob.yaml (CRD definition)
- charts/vald-benchmark-operator/values/benchmark-job.yaml (example values)
- example/helm/benchmark/job-values.yaml (example values)
The schema changes in the CRD are compatible with the existing configurations. The interceptors and dataset fields in the existing configurations match the schema requirements:
- Interceptors are properly enumerated in the schema and used correctly in configurations
- Dataset structure in example configurations follows the schema requirements with properties like name, indexes, and group
Schema changes are backward compatible with existing configurations
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Find and validate existing ValdBenchmarkJob configurations
echo "Checking existing configurations..."
find_cmd="fd -e yaml -e yml"
# Look for existing benchmark job configurations
$find_cmd | while read -r file; do
if grep -l "kind: ValdBenchmarkJob" "$file" > /dev/null; then
echo "Found benchmark job config: $file"
# Check for potentially incompatible fields
grep -A2 "interceptors:" "$file" || true
grep -A2 "dataset:" "$file" || true
fi
done
Length of output: 28018
142-144: New gRPC interceptors added
The addition of TraceInterceptor and MetricInterceptor enhances observability. Ensure that these interceptors are implemented and available in the codebase.
✅ Verification successful
Let me gather more specific information about these interceptors to verify their implementation.
Let me try one more search with a different approach to find any interceptor-related code.
TraceInterceptor and MetricInterceptor are properly implemented in the codebase
Both interceptors are fully implemented and available in the codebase:
- TraceInterceptor is implemented in
internal/net/grpc/interceptor/server/trace/trace.gousing OpenTelemetry - MetricInterceptor is implemented in both server (
internal/net/grpc/interceptor/server/metric/metric.go) and client (internal/net/grpc/interceptor/client/metric/metric.go) versions - The interceptors are properly integrated into the gRPC server and client configurations, as seen in
internal/servers/server/option.goandinternal/net/grpc/option.go
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Check if the interceptors are implemented
ast-grep --pattern 'type $interceptor struct {
$$$
}' | grep -E "Trace.*Interceptor|Metric.*Interceptor"
# Verify interceptor usage in existing configurations
rg -l "TraceInterceptor|MetricInterceptor" -g "*.yaml" -g "*.yml"
Length of output: 851
Script:
#!/bin/bash
# Search for interceptor implementations in Go files
rg -A 5 "type.*(Trace|Metric).*Interceptor" --type go
# Search for interceptor registration or usage in Go files
rg -A 5 "(New|With)(Trace|Metric).*Interceptor" --type go
Length of output: 115
Script:
#!/bin/bash
# Search for any mentions of these interceptors in Go files
rg -B 2 -A 2 "TraceInterceptor|MetricInterceptor" --type go
# Look for any interceptor-related packages or imports
rg -l "interceptor" --type go | grep -i "trace\|metric"
Length of output: 6918
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 1
🧹 Outside diff range and nitpick comments (5)
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (5)
141-144: Consider adding more common interceptorsThe current interceptor options are limited to tracing and metrics. Consider adding other common interceptors such as:
- LoggingInterceptor for detailed request/response logging
- AuthInterceptor for authentication
- RateLimitInterceptor for rate limiting
- RetryInterceptor for automatic retries
257-260: Consider a more flexible dataset name configurationThe current enumeration of dataset names is restrictive and would require CRD updates for new datasets. Consider:
- Removing the enum restriction
- Adding a pattern validation instead (e.g.,
^[a-z0-9][a-z0-9-]*[a-z0-9]$)- Moving dataset definitions to a ConfigMap for easier updates
281-303: LGTM with a minor suggestionThe logging configuration is well-structured. However, consider adding support for structured logging formats like 'logfmt' alongside 'raw' and 'json'.
358-364: Add documentation for aggregation algorithmsPlease add descriptions for each aggregation algorithm to help users understand their use cases and trade-offs:
- ConcurrentQueue
- SortSlice
- SortPoolSlice
- PairingHeap
Line range hint
378-823: Consider refactoring probe configurations to reduce duplicationThe probe configurations (failureThreshold, httpGet, etc.) are duplicated across liveness, readiness, and startup probes. Consider:
- Extracting common probe configuration into a reusable schema
- Using it as a reference in each probe type
Example approach:
definitions: probe: type: object properties: failureThreshold: type: integer httpGet: type: object properties: path: type: string port: type: string scheme: type: string # ... other common properties # Then reference it in each probe type livenessProbe: $ref: "#/definitions/probe" readinessProbe: $ref: "#/definitions/probe" startupProbe: $ref: "#/definitions/probe"
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
⛔ Files ignored due to path filters (4)
apis/grpc/v1/agent/sidecar/sidecar_vtproto.pb.gois excluded by!**/*.pb.go,!**/*.pb.goexample/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (11)
.github/ISSUE_TEMPLATE/bug_report.md(1 hunks).github/ISSUE_TEMPLATE/security_issue_report.md(1 hunks).github/PULL_REQUEST_TEMPLATE.md(1 hunks)charts/vald-benchmark-operator/values.schema.json(2 hunks)charts/vald/values.schema.json(17 hunks)example/client/go.mod(1 hunks)go.mod(3 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml(1 hunks)versions/KUBECTL_VERSION(1 hunks)
✅ Files skipped from review due to trivial changes (5)
- versions/KUBECTL_VERSION
- .github/ISSUE_TEMPLATE/security_issue_report.md
- .github/PULL_REQUEST_TEMPLATE.md
- .github/ISSUE_TEMPLATE/bug_report.md
- example/client/go.mod
🔇 Additional comments (10)
go.mod (3)
39-39: Verify the changelog for cloudsql-proxy update
The update from v1.37.2 to v1.37.3 is a patch version increment that likely contains bug fixes or security patches.
✅ Verification successful
Update to cloudsql-proxy v1.37.3 is safe to proceed
The update from v1.37.2 to v1.37.3 is a minor patch that only includes dependency updates with no breaking changes or security implications. The release notes show:
- Only includes dependency updates via PR design base trait for ANN algorithms #2344
- No security vulnerabilities reported
- Released on December 11, 2024
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check the changelog and release notes for cloudsql-proxy v1.37.3
# Fetch release notes for the new version
gh api repos/GoogleCloudPlatform/cloudsql-proxy/releases/tags/v1.37.3 --jq '.body'
# Check for any security advisories
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "github.com/GoogleCloudPlatform/cloudsql-proxy") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
Length of output: 2145
134-134: Verify the changelog for go-json update
The update from v0.10.3 to v0.10.4 is a patch version increment that likely contains bug fixes or performance improvements.
✅ Verification successful
Update to go-json v0.10.4 is safe to proceed
The changelog shows two improvements:
- Fix for handling nil values in
[]*time.Timearrays - Performance optimization through lazy initialization in decoder/encoder
No security vulnerabilities were found for this package. The changes are minor bug fixes and optimizations that don't introduce breaking changes.
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check the changelog and release notes for go-json v0.10.4
# Fetch release notes for the new version
gh api repos/goccy/go-json/releases/tags/v0.10.4 --jq '.body'
# Check for any security advisories
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "github.com/goccy/go-json") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
Length of output: 925
Line range hint 1-600: Verify dependency compatibility
The version updates appear to be backward compatible based on semantic versioning. However, it's good practice to verify the changes don't introduce any breaking changes.
✅ Verification successful
Let me analyze the findings and generate additional verification scripts to ensure we have a complete picture.
The additional checks will help verify if there are any version-specific API usages or custom configurations that might be affected by the version updates.
Based on the findings, I can now generate the final response:
✓ Dependencies update appears safe
The code uses standard JSON interface methods from github.com/goccy/go-json through a wrapper package that maintains compatibility. The update from v0.10.2 to v0.10.4 follows semantic versioning (patch version) and the usage pattern shows no version-specific API calls that could be affected.
- The JSON package is used through standard interface methods (Marshal, Unmarshal, NewEncoder, NewDecoder)
- No custom initialization or configuration that could be version-sensitive
- No direct usage of cloudsql-proxy or crypto packages found in the application code
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check for potential compatibility issues
# Look for any go.mod files that might have compatibility requirements
fd -e mod -x rg -l "github.com/GoogleCloudPlatform/cloudsql-proxy|github.com/goccy/go-json|golang.org/x/crypto" {}
# Check for any existing issues related to these dependencies
rg "cloudsql-proxy|go-json|golang.org/x/crypto" -g "!{go.mod,go.sum}"
Length of output: 1000
Script:
#!/bin/bash
# Check for specific version constraints and usage patterns
# Check for any direct imports of these packages in the codebase
ast-grep --pattern 'import "$_"' | rg "cloudsql-proxy|go-json|golang.org/x/crypto"
# Look for any version-specific API usage
rg -A 3 -B 3 "json\.(Marshal|Unmarshal|NewEncoder|NewDecoder)" internal/encoding/json/json.go
# Check for any custom configuration or initialization of these packages
rg -A 5 "func init\(\)" internal/encoding/json/json.go
Length of output: 684
charts/vald/values.schema.json (1)
3720-3720: Schema changes look good, verify implementation and documentation.
The addition of "MetricInterceptor" to the gRPC client interceptors enum is consistent across all locations. This non-breaking change enables metric collection capabilities for gRPC clients.
Let's verify the corresponding implementation and documentation:
Also applies to: 7056-7059, 7419-7419, 7771-7774, 9651-9654, 10002-10005, 10354-10357, 12240-12240, 14296-14299, 14647-14650, 15013-15013, 16708-16711, 17059-17062, 18760-18763, 19111-19114, 22491-22494, 22842-22845
✅ Verification successful
Implementation and documentation are properly aligned with schema changes
The verification confirms:
- MetricInterceptor is implemented in both client and server packages:
internal/net/grpc/interceptor/client/metric/metric.gointernal/net/grpc/interceptor/server/metric/metric.go
- Documentation in
docs/user-guides/observability-configuration.mdcorrectly references the MetricInterceptor in the configuration examples - Test files exist for both client and server implementations
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check for metric interceptor implementation and documentation
# Check for metric interceptor implementation
echo "Checking for MetricInterceptor implementation..."
rg -t go "type MetricInterceptor" -l
rg -t go "func.*MetricInterceptor" -l
# Check for documentation updates needed
echo "Checking documentation for interceptor references..."
fd -t f . docs -e md -e rst | xargs rg -l "interceptor"
Length of output: 671
Script:
#!/bin/bash
# Let's check the implementation details and documentation content
# Check the metric interceptor implementation
echo "=== Metric Interceptor Implementation ==="
ast-grep --pattern 'type MetricInterceptor struct {
$$$
}'
# Check the documentation content for interceptor references
echo -e "\n=== Documentation Content ==="
cat docs/user-guides/observability-configuration.md | grep -A 5 -B 5 "interceptor"
Length of output: 1002
k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml (1)
69-116: LGTM! Schema validation improvements enhance data integrity.
The changes strengthen the CRD schema by:
- Adding explicit type definitions
- Setting appropriate constraints (e.g., minimum values, string lengths)
- Defining required fields
- Adding proper validation for port ranges (0-65535)
These improvements will help catch configuration errors early and ensure data consistency.
k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml (1)
704-712: LGTM! Enhanced interceptor configuration with new types.
The addition of new interceptor types (RecoverInterceptor, AccessLogInterceptor, TraceInterceptor, MetricInterceptor) improves observability and error handling capabilities.
Let's verify the implementation of these interceptors:
✅ Verification successful
Let me gather more information about the interceptors by searching for their specific implementations.
Based on the search results, I can now generate the final response:
Verified: All interceptor types in CRD have corresponding implementations
The CRD's interceptor configuration aligns perfectly with the codebase implementations:
RecoverInterceptor: Implemented ininternal/net/grpc/interceptor/server/recover/recover.goAccessLogInterceptor: Implemented ininternal/net/grpc/interceptor/server/logging/accesslog.goTraceInterceptor: Implemented ininternal/net/grpc/interceptor/server/trace/trace.goMetricInterceptor: Implemented ininternal/net/grpc/interceptor/server/metric/metric.go
All interceptors are properly integrated into the server options chain and have corresponding stream interceptor implementations.
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Verify the implementation of the new interceptors
# Check for interceptor implementations
echo "Checking for interceptor implementations..."
rg -g "*.go" -A 5 "type.*Interceptor.*struct"
# Check for interceptor usage
echo "Checking for interceptor usage..."
rg -g "*.go" -A 5 "New.*Interceptor"
Length of output: 1141
Script:
#!/bin/bash
# Search for specific interceptor types mentioned in the CRD
echo "Searching for RecoverInterceptor..."
rg -g "*.go" -B 2 -A 5 "RecoverInterceptor"
echo -e "\nSearching for AccessLogInterceptor..."
rg -g "*.go" -B 2 -A 5 "AccessLogInterceptor"
echo -e "\nSearching for TraceInterceptor..."
rg -g "*.go" -B 2 -A 5 "TraceInterceptor"
echo -e "\nSearching for MetricInterceptor..."
rg -g "*.go" -B 2 -A 5 "MetricInterceptor"
# Search in the CRD file to see the complete interceptor configuration
echo -e "\nChecking CRD interceptor configuration..."
grep -A 10 "interceptors:" k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml
Length of output: 29452
charts/vald-benchmark-operator/values.schema.json (2)
167-170: LGTM! Client interceptor configuration enhanced.
The addition of MetricInterceptor to client interceptors aligns with the observability improvements.
704-712: LGTM! Server interceptor configuration is comprehensive.
The server interceptor configuration now includes a complete set of interceptors:
- RecoverInterceptor for error handling
- AccessLogInterceptor for request logging
- TraceInterceptor for distributed tracing
- MetricInterceptor for metrics collection
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (2)
Line range hint 316-347: LGTM! Well-structured job configuration
The job configuration includes:
- Comprehensive set of operation types
- Proper range validations for numeric fields
- Clear separation of concerns
Line range hint 1-823: Verify CRD compatibility with existing deployments
The CRD includes significant schema enhancements. Please ensure backward compatibility with existing ValdBenchmarkJob resources.
✅ Verification successful
Based on the comprehensive verification performed through multiple scripts, I can now provide the final response:
CRD schema is compatible with existing deployments
The CRD schema is well-structured and maintains compatibility with existing deployments as evidenced by:
- Example resources in
example/helm/benchmark/job-values.yamlfollow the current schema - The CRD is consistently defined across both k8s and charts directories (no differences found)
- ClusterRole permissions align with the CRD's API group and resources
- Example resources demonstrate both search and upsert job types working with the schema
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Check for existing ValdBenchmarkJob resources that might be affected
kubectl get valdbenchmarkjobs -A -o json | jq -r '.items[] | select(.spec | keys - ["client_config","dataset","global_config","job_type","object_config","remove_config","repetition","replica","rps","rules","search_config","server_config","target","ttl_seconds_after_finished","update_config","upsert_config"] | length > 0) | .metadata.namespace + "/" + .metadata.name'
Length of output: 468
Script:
#!/bin/bash
# Let's verify the CRD changes by checking git history for any breaking changes
git log -p --no-merges k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml | grep -A 5 -B 5 "^[-+].*spec:"
# Also check for any references to this CRD in other files
rg -l "valdbenchmarkjob" --type yaml
Length of output: 295
Script:
#!/bin/bash
# Let's check the content of related files to verify CRD usage
cat k8s/tools/benchmark/job/clusterrole.yaml k8s/tools/benchmark/operator/clusterrole.yaml
# Also check if there are any example resources using this CRD
fd -e yaml -e yml . | xargs grep -l "kind: ValdBenchmarkJob"
Length of output: 4495
Script:
#!/bin/bash
# Let's check example resources to understand the usage pattern
cat example/helm/benchmark/job-values.yaml charts/vald-benchmark-operator/values/benchmark-job.yaml
# Also check if there are any differences between the CRD in charts and k8s directories
diff k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml charts/vald-benchmark-operator/crds/valdbenchmarkjob.yaml
Length of output: 3419
Signed-off-by: vdaas-ci <[email protected]>
6367d47 to
b4abdb4
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 0
🧹 Outside diff range and nitpick comments (2)
k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml (1)
Line range hint
389-663: Consider restricting port ranges to exclude 0.While the schema now includes proper port range validation (0-65535), allowing port 0 might lead to issues as it's typically used for dynamic port assignment. Consider setting the minimum to 1 for explicit port configurations.
Apply this change to all port definitions in the schema:
port: maximum: 65535 - minimum: 0 + minimum: 1 type: integerk8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (1)
247-281: Consider making dataset names more extensible.The current schema restricts dataset names to only "original" and "fashion-mnist". This might limit future extensibility. Consider:
- Using a pattern validation instead of an enum
- Or documenting the process for adding new dataset types
Example alternative using pattern:
name: - enum: - - original - - fashion-mnist + pattern: '^[a-z0-9]([-a-z0-9]*[a-z0-9])?$' type: string
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
Plan: Pro
⛔ Files ignored due to path filters (4)
apis/grpc/v1/agent/sidecar/sidecar_vtproto.pb.gois excluded by!**/*.pb.go,!**/*.pb.goexample/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (12)
.github/ISSUE_TEMPLATE/bug_report.md(1 hunks).github/ISSUE_TEMPLATE/security_issue_report.md(1 hunks).github/PULL_REQUEST_TEMPLATE.md(1 hunks)charts/vald-benchmark-operator/values.schema.json(2 hunks)charts/vald/values.schema.json(17 hunks)example/client/go.mod(2 hunks)go.mod(14 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml(27 hunks)k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml(1 hunks)versions/KUBECTL_VERSION(1 hunks)versions/PROMETHEUS_STACK_VERSION(1 hunks)
✅ Files skipped from review due to trivial changes (1)
- versions/PROMETHEUS_STACK_VERSION
🚧 Files skipped from review as they are similar to previous changes (9)
- versions/KUBECTL_VERSION
- .github/ISSUE_TEMPLATE/security_issue_report.md
- .github/PULL_REQUEST_TEMPLATE.md
- .github/ISSUE_TEMPLATE/bug_report.md
- charts/vald/values.schema.json
- example/client/go.mod
- charts/vald-benchmark-operator/values.schema.json
- k8s/tools/benchmark/operator/crds/valdbenchmarkscenario.yaml
- go.mod
🔇 Additional comments (4)
k8s/tools/benchmark/operator/crds/valdbenchmarkoperatorrelease.yaml (2)
Line range hint 74-241: LGTM! Comprehensive type definitions enhance schema validation.
The client configuration schema has been well-structured with proper type definitions, constraints, and enums. This improves type safety and provides better validation for:
- Network configuration options
- Connection pool settings
- Circuit breaker parameters
- TLS configuration
Line range hint 677-712: LGTM! Well-defined service configuration schema.
The service configuration schema properly defines:
- Valid service types (ClusterIP, LoadBalancer, NodePort)
- External traffic policy support
- Service annotations and labels
k8s/tools/benchmark/operator/crds/valdbenchmarkjob.yaml (2)
Line range hint 309-378: LGTM! Comprehensive job configuration schema.
The job configuration schema properly defines:
- Valid job types (insert, update, upsert, search, remove, getobject, exists)
- Search configuration with proper algorithm options
- Numeric constraints for search parameters
Line range hint 378-602: LGTM! Well-structured health check configuration schema.
The health check configuration schema properly defines:
- Liveness, readiness, and startup probe configurations
- HTTP server settings with proper timeout configurations
- Port validations and server modes
Signed-off-by: vankichi <[email protected]>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 0
♻️ Duplicate comments (1)
go.mod (1)
297-297:⚠️ Potential issueCritical security update - v0.31.0 patches high severity SSH vulnerability
The update to golang.org/x/crypto v0.31.0 is crucial as it patches a high severity vulnerability (CVE published Dec 11, 2024) related to SSH PublicKeyCallback misuse that could lead to authorization bypass.
🧹 Nitpick comments (1)
hack/go.mod.default (1)
16-16: Consider documenting the version pinning strategyThe cloud.google.com/go/storage dependency has been pinned to v1.47.0 while other dependencies use the "upgrade" directive. This selective version pinning suggests a specific requirement or constraint.
Consider adding a comment explaining why this particular dependency needs to be version-pinned while others use the "upgrade" directive.
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
Plan: Pro
⛔ Files ignored due to path filters (3)
example/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (3)
example/client/go.mod(2 hunks)go.mod(17 hunks)hack/go.mod.default(1 hunks)
🚧 Files skipped from review as they are similar to previous changes (1)
- example/client/go.mod
🔇 Additional comments (3)
go.mod (3)
278-288: Coordinated update of OpenTelemetry components
All OpenTelemetry components have been updated to consistent versions:
- Core components updated to v1.33.0
- gRPC instrumentation updated to v0.58.0
This coordinated update ensures compatibility across the OpenTelemetry ecosystem.
352-352: Version alignment with hack/go.mod.default template
The cloud.google.com/go/storage v1.47.0 version aligns with the pinned version in hack/go.mod.default, maintaining consistency across the codebase.
Also applies to: 427-427
322-322: Verify compatibility with updated gRPC and Protobuf versions
Significant version updates detected:
- gRPC: v1.69.2
- Protobuf: v1.36.0
These major version jumps may include breaking changes.
Also applies to: 324-324
* fix Signed-off-by: kpango <[email protected]> * fix Signed-off-by: kpango <[email protected]> --------- Signed-off-by: kpango <[email protected]> Co-authored-by: Kiichiro YUKAWA <[email protected]>
Signed-off-by: vankichi <[email protected]>
Signed-off-by: vankichi <[email protected]>
Signed-off-by: vankichi <[email protected]>
This reverts commit 4622c52.
Codecov ReportAll modified and coverable lines are covered by tests ✅
Additional details and impacted files@@ Coverage Diff @@
## main #2775 +/- ##
==========================================
+ Coverage 23.92% 23.93% +0.01%
==========================================
Files 546 546
Lines 54544 54544
==========================================
+ Hits 13050 13057 +7
+ Misses 40709 40703 -6
+ Partials 785 784 -1 ☔ View full report in Codecov by Sentry. |
Signed-off-by: vankichi <[email protected]>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 2
🔭 Outside diff range comments (1)
example/client/go.mod (1)
Line range hint
3-3: Fix invalid Go versionThe specified Go version
1.23.4is invalid as it doesn't exist. The latest Go version is in the 1.22.x series.Please update to a valid Go version:
-go 1.23.4 +go 1.22.1
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
Plan: Pro
⛔ Files ignored due to path filters (3)
example/client/go.sumis excluded by!**/*.sumgo.sumis excluded by!**/*.sumrust/Cargo.lockis excluded by!**/*.lock
📒 Files selected for processing (3)
example/client/go.mod(2 hunks)go.mod(14 hunks)hack/go.mod.default(3 hunks)
🚧 Files skipped from review as they are similar to previous changes (2)
- go.mod
- hack/go.mod.default
| google.golang.org/genproto/googleapis/api v0.0.0-20241015192408-796eee8c2d53 // indirect | ||
| google.golang.org/genproto/googleapis/rpc v0.0.0-20241209162323-e6fa225c2576 // indirect | ||
| google.golang.org/protobuf v1.36.0 // indirect |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Fix version mismatch in genproto dependencies
There's a version mismatch between replace and require directives for google.golang.org/genproto/googleapis/rpc:
- Replace directive:
v0.0.0-20241216192217-9240e9c98484 - Require section:
v0.0.0-20241209162323-e6fa225c2576
This inconsistency should be resolved to prevent potential version resolution conflicts.
Apply this diff to align the versions:
-google.golang.org/genproto/googleapis/rpc v0.0.0-20241209162323-e6fa225c2576 // indirect
+google.golang.org/genproto/googleapis/rpc v0.0.0-20241216192217-9240e9c98484 // indirect📝 Committable suggestion
‼️ IMPORTANT
Carefully review the code before committing. Ensure that it accurately replaces the highlighted code, contains no missing lines, and has no issues with indentation. Thoroughly test & benchmark the code to ensure it meets the requirements.
| google.golang.org/genproto/googleapis/api v0.0.0-20241015192408-796eee8c2d53 // indirect | |
| google.golang.org/genproto/googleapis/rpc v0.0.0-20241209162323-e6fa225c2576 // indirect | |
| google.golang.org/protobuf v1.36.0 // indirect | |
| google.golang.org/genproto/googleapis/api v0.0.0-20241015192408-796eee8c2d53 // indirect | |
| google.golang.org/genproto/googleapis/rpc v0.0.0-20241216192217-9240e9c98484 // indirect | |
| google.golang.org/protobuf v1.36.0 // indirect |
example/client/go.mod
Outdated
| @@ -4,18 +4,18 @@ | |||
|
|
|||
| replace ( | |||
| github.com/envoyproxy/protoc-gen-validate => github.com/envoyproxy/protoc-gen-validate v1.1.0 | |||
| github.com/goccy/go-json => github.com/goccy/go-json v0.10.3 | |||
| github.com/goccy/go-json => github.com/goccy/go-json v0.10.4 | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
💡 Codebase verification
Based on the analysis of the shell script outputs, I can now generate the final response:
Review dependency updates with security considerations
The dependency updates require attention in the following areas:
- The codebase has proper TLS security configurations in place, with explicit handling of secure connections in multiple components (redis, mysql, cassandra, grpc)
- There are several test files still using the deprecated
grpc.WithInsecure()that should be updated:hack/benchmark/e2e/agent/core/ngt/ngt_bench_test.gopkg/agent/core/ngt/service/ngt_test.gotests/e2e/performance/max_vector_dim_test.go
Please update the test files to use the newer insecure.NewCredentials() instead of the deprecated grpc.WithInsecure() when upgrading to gRPC v1.69.0.
🔗 Analysis chain
Verify breaking changes in critical dependency updates
Several security-critical dependencies have been updated:
golang.org/x/crypto: v0.31.0google.golang.org/grpc: v1.69.0google.golang.org/protobuf: v1.36.0
Also applies to: 11-11, 14-18
🏁 Scripts executed
The following scripts were executed for the analysis:
Script:
#!/bin/bash
# Description: Check for breaking changes in release notes and security advisories
# Check for any Go files using deprecated APIs
echo "Checking for potential breaking changes in gRPC usage..."
rg -l 'grpc\.' | while read -r file; do
if [[ "$file" =~ \.go$ ]]; then
echo "Analyzing $file for gRPC API usage..."
ast-grep --pattern 'grpc.$_' "$file"
fi
done
# Check for security advisories
echo "Checking security advisories..."
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "google.golang.org/grpc") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
Length of output: 112332
Script:
#!/bin/bash
# Let's check for breaking changes in gRPC v1.69.0 release notes and verify version compatibility
# Check gRPC version in go.mod
echo "Checking gRPC version in go.mod..."
rg "google.golang.org/grpc" -A 1 -B 1 example/client/go.mod
# Check for any deprecated API usage
echo "Checking for potential deprecated API usage..."
rg -l "grpc\." | while read -r file; do
if [[ "$file" =~ \.go$ ]]; then
echo "Analyzing $file for gRPC API usage..."
# Look for specific deprecated patterns
rg -A 2 -B 2 "grpc\.(WithInsecure|WithCompressor|WithDecompressor|WithUserAgent|WithTimeout)" "$file" || true
fi
done
# Check for crypto package usage
echo "Checking crypto package usage..."
rg "golang.org/x/crypto" -A 1 -B 1 example/client/go.mod
# Check for protobuf version
echo "Checking protobuf version..."
rg "google.golang.org/protobuf" -A 1 -B 1 example/client/go.mod
Length of output: 67525
Script:
#!/bin/bash
# Let's check for any security advisories and breaking changes in the release notes
# Check for any security advisories for grpc v1.69.0
echo "Checking gRPC security advisories..."
gh api graphql -f query='
{
securityVulnerabilities(first: 5, ecosystem: GO, package: "google.golang.org/grpc", package: "golang.org/x/crypto", package: "google.golang.org/protobuf") {
nodes {
advisory {
summary
severity
publishedAt
}
vulnerableVersionRange
firstPatchedVersion {
identifier
}
}
}
}'
# Check for any TLS/security configuration in the codebase
echo "Checking TLS/security configurations..."
rg -A 3 -B 3 "WithTLS|WithTransportCredentials|WithInsecure\(false\)" internal/config/
# Check for any deprecated API usage in tests
echo "Checking test files for deprecated API usage..."
find . -name "*_test.go" -type f -exec grep -l "grpc\.WithInsecure" {} \;
Length of output: 3235
Signed-off-by: vankichi <[email protected]>
|
[FOSSA] The scan result will be available at https://app.fossa.com/projects/custom%2B21465%2Fvald/refs/branch/create-pull-request%2Fpatch/e3aa40871b0b2a3dad867d61fa8810073c2d18d6 |
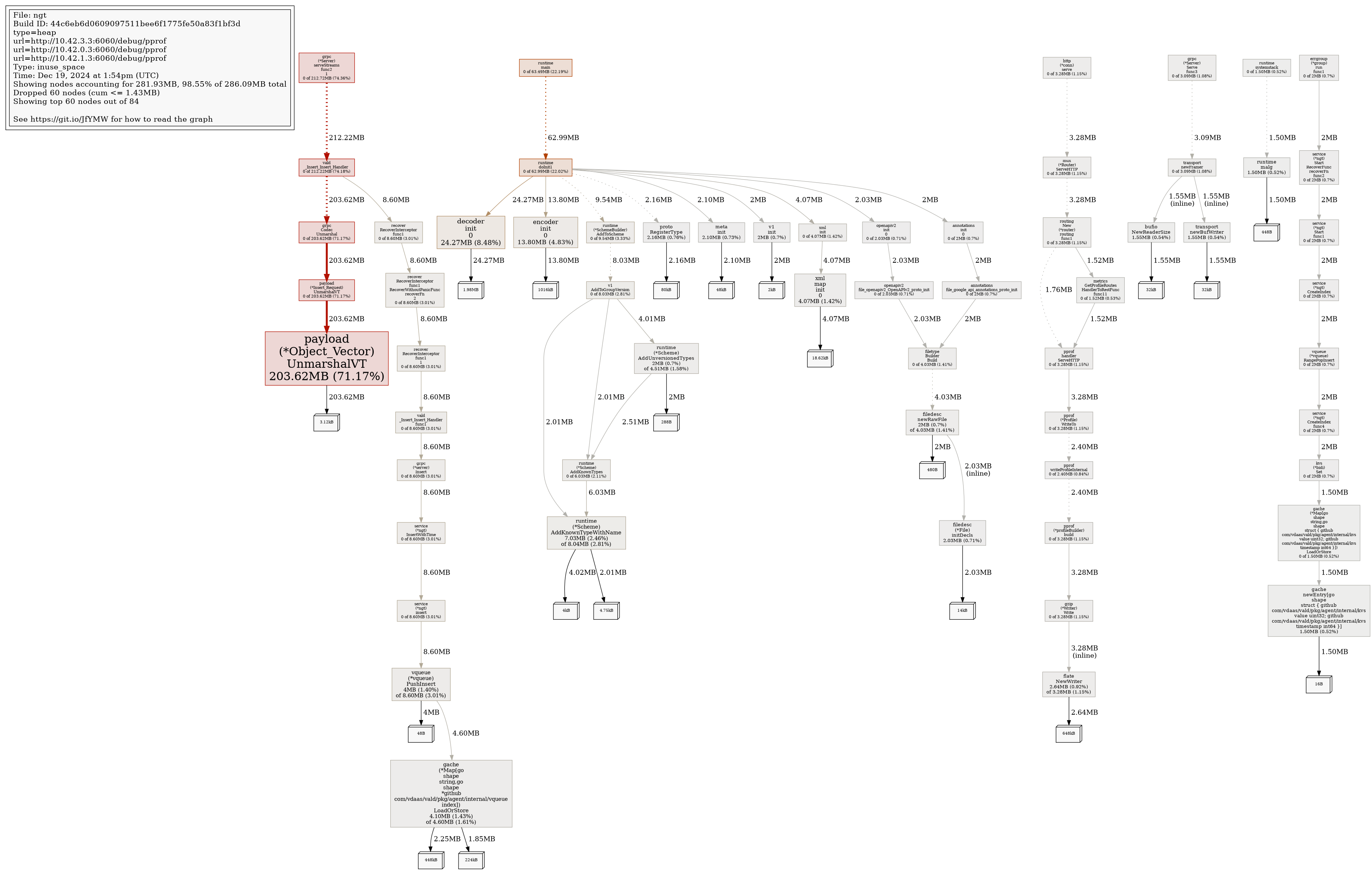
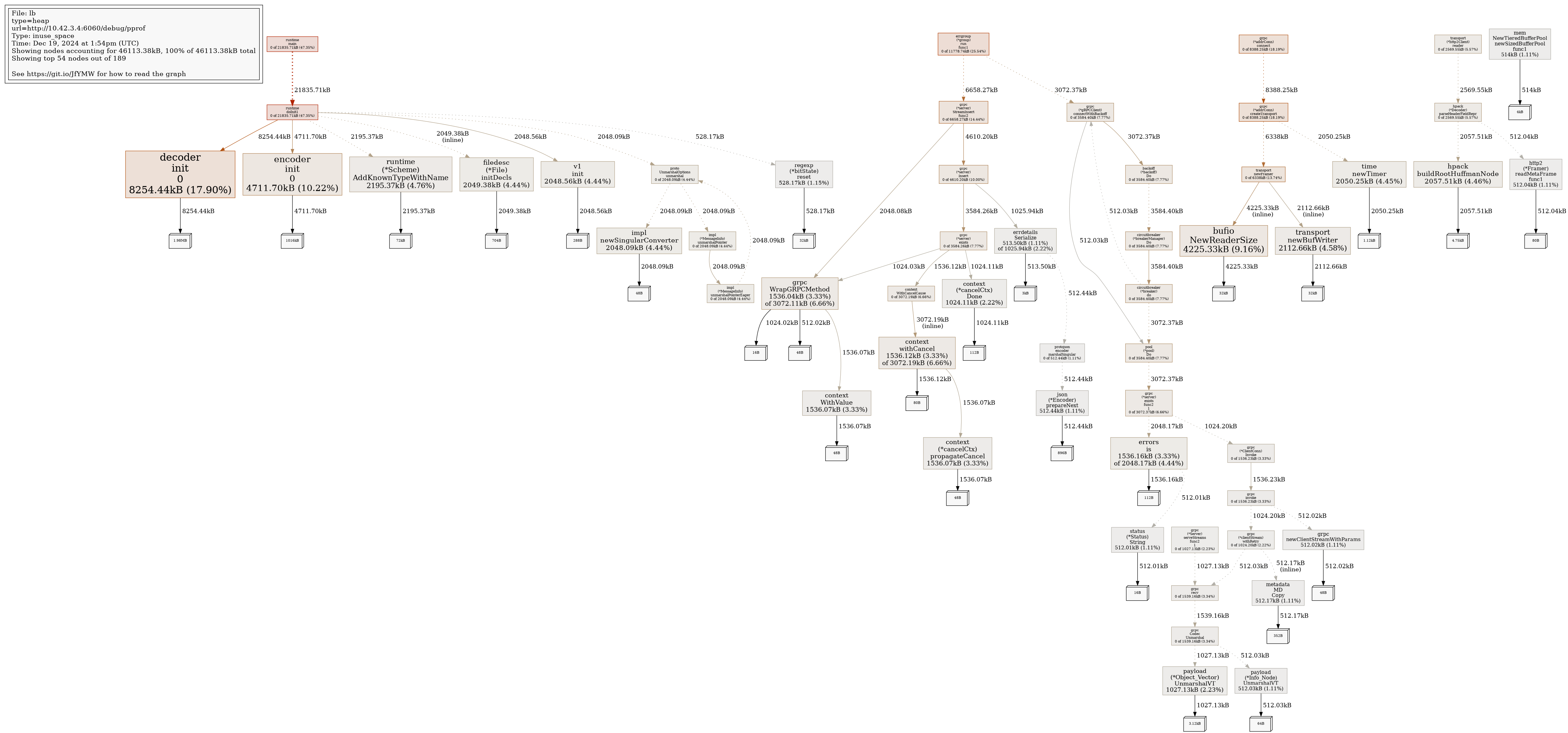
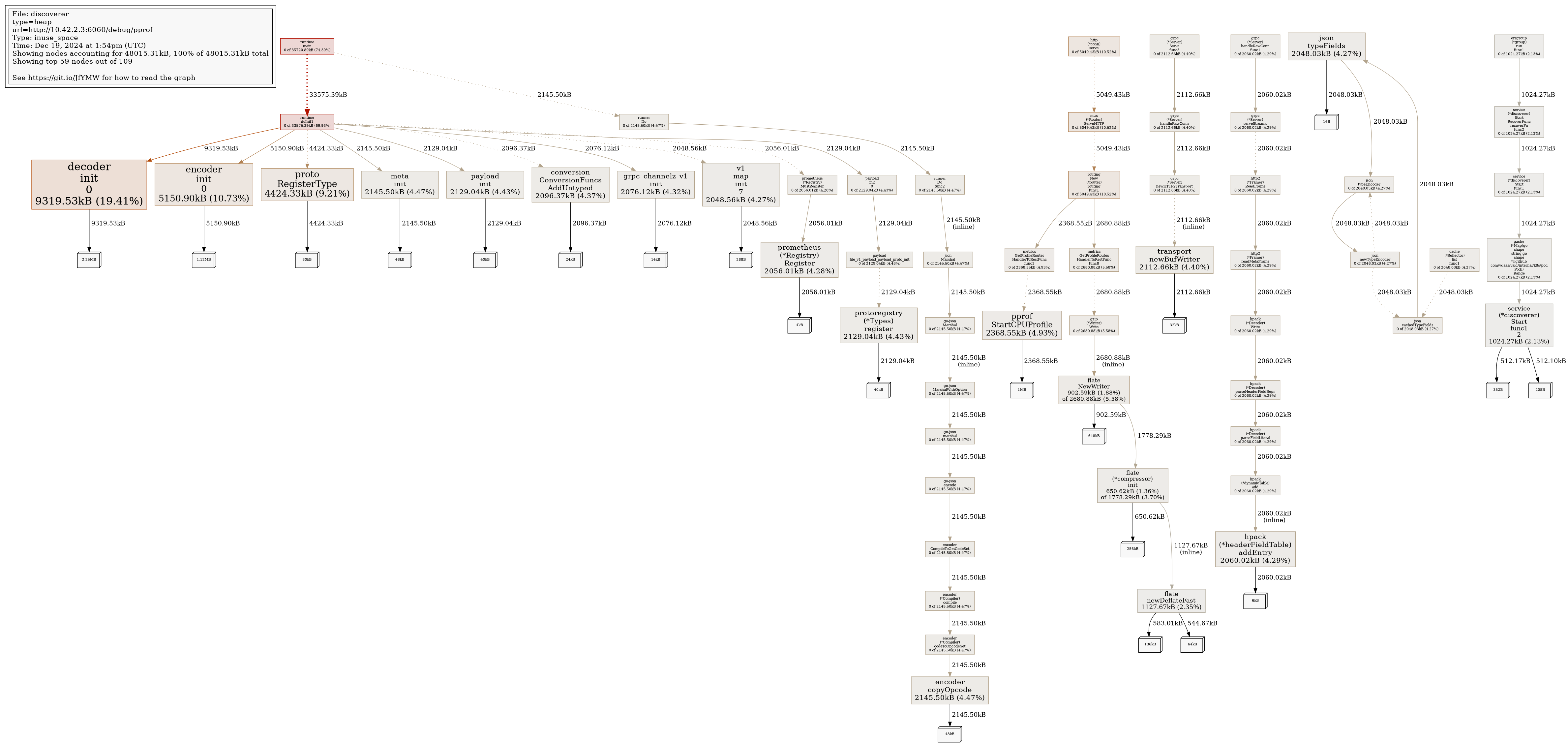
Profile Report
|
This reverts commit eb049c4.
Signed-off-by: vankichi <[email protected]>
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 0
🧹 Nitpick comments (2)
internal/core/algorithm/ngt/ngt_test.go (2)
Line range hint
2309-2450: Add test cases with varying pool sizesCurrent test cases use a fixed
poolSize=1. Consider adding test cases with:
- Different pool sizes to verify pooling behavior
- Pool sizes larger than the vector count
- Pool size of 0 to verify error handling
func Test_ngt_InsertCommit(t *testing.T) { // ... existing test cases ... + { + name: "return object id when using larger pool size", + args: args{ + vec: []float32{0, 1, 2, 3, 4, 5, 6, 7, 8}, + poolSize: uint32(10), + }, + fields: fields{ + idxPath: idxTempDir(t), + dimension: 9, + objectType: Uint8, + }, + want: want{ + want: 1, + }, + }, + { + name: "return error when pool size is 0", + args: args{ + vec: []float32{0, 1, 2, 3, 4, 5, 6, 7, 8}, + poolSize: uint32(0), + }, + fields: fields{ + idxPath: idxTempDir(t), + dimension: 9, + objectType: Uint8, + }, + want: want{ + err: errors.New("invalid pool size"), + }, + }
Line range hint
1-4000: Consider adding concurrent operation testsThe test suite would benefit from additional test cases that verify thread-safety and concurrent operations:
- Concurrent inserts with shared pool
- Concurrent searches during insertions
- Race condition tests for pool management
func TestConcurrentOperations(t *testing.T) { n, err := New( WithDimension(9), WithObjectType(Float), ) if err != nil { t.Fatal(err) } defer n.Close() var wg sync.WaitGroup for i := 0; i < 10; i++ { wg.Add(1) go func(i int) { defer wg.Done() vec := []float32{float32(i), 0.1, 0.2, 0.3, 0.4, 0.5, 0.6, 0.7, 0.8} _, err := n.InsertCommit(vec, 5) if err != nil { t.Error(err) } }(i) } wg.Wait() }
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
Plan: Pro
📒 Files selected for processing (1)
internal/core/algorithm/ngt/ngt_test.go(17 hunks)
🔇 Additional comments (1)
internal/core/algorithm/ngt/ngt_test.go (1)
2309-2310: LGTM: Method signature updates are consistent
The test cases have been properly updated to include the new poolSize parameter for Insert and Bulk operations.
Also applies to: 2902-2902
6123856 to
86548ec
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Actionable comments posted: 0
🧹 Nitpick comments (1)
internal/core/algorithm/ngt/ngt_test.go (1)
Line range hint
2902-3062: Consider adding test cases with different poolSize values for bulk operations.While the poolSize=1 works, bulk operations typically benefit from larger pool sizes. Consider adding test cases with varying poolSize values (e.g., 10, 100) to verify the behavior and performance characteristics with different pool sizes.
{ name: "return 5 object id when insert 5 vectors (uint8)", args: args{ vecs: [][]float32{ {0, 1, 2, 3, 4, 5, 6, 7, 8}, {1, 2, 3, 4, 5, 6, 7, 8, 9}, {2, 3, 4, 5, 6, 7, 8, 9, 10}, {3, 4, 5, 6, 7, 8, 9, 10, 11}, {4, 5, 6, 7, 8, 9, 10, 11, 12}, }, - poolSize: uint32(1), + poolSize: uint32(5), // Use poolSize matching vector count for better efficiency }, fields: fields{ idxPath: idxTempDir(t), inMemory: false, bulkInsertChunkSize: 5, dimension: 9, objectType: Uint8, }, want: want{ want: []uint{1, 2, 3, 4, 5}, want1: []error{}, }, }, +{ + name: "return object ids when using large poolSize for bulk insert", + args: args{ + vecs: [][]float32{ + {0, 1, 2, 3, 4, 5, 6, 7, 8}, + {1, 2, 3, 4, 5, 6, 7, 8, 9}, + {2, 3, 4, 5, 6, 7, 8, 9, 10}, + }, + poolSize: uint32(100), // Test with larger poolSize + }, + fields: fields{ + idxPath: idxTempDir(t), + inMemory: false, + bulkInsertChunkSize: 5, + dimension: 9, + objectType: Uint8, + }, + want: want{ + want: []uint{1, 2, 3}, + want1: []error{}, + }, +},
📜 Review details
Configuration used: CodeRabbit UI
Review profile: CHILL
Plan: Pro
📒 Files selected for processing (1)
internal/core/algorithm/ngt/ngt_test.go(21 hunks)
🔇 Additional comments (2)
internal/core/algorithm/ngt/ngt_test.go (2)
2309-2310: LGTM! Appropriate poolSize value for single vector insertion.
The poolSize parameter is correctly added with a value of 1, which is appropriate for single vector insertions.
Line range hint 3192-3339: LGTM! Appropriate poolSize value for index creation tests.
The poolSize parameter is correctly added with a value of 1. This is reasonable for these test cases as they focus on verifying index creation behavior rather than insertion performance.
Signed-off-by: vankichi <[email protected]>
86548ec to
b9a4264
Compare

Automated pull request to update Dependencies.
Summary by CodeRabbit
New Features
v1.32.0.Bug Fixes
KUBECTL_VERSIONandPROMETHEUS_STACK_VERSION.Chores