-
Notifications
You must be signed in to change notification settings - Fork 503
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
ci-signal-reporter, automatically generate weekly ci signal report #2443
Comments
|
/assign @voigt |
|
I think we need to get the github information from the new project board before we make progress here. There is an issue open ref #2396 and slack thread |
|
@voigt #2454 has been merged I think we are good to start working on this issue. Ref google group k/dev for CI Signal report examples |
|
/milestone v1.24 |
|
/unassign @voigt |
|
After one-on-one talks with @leonardpahlke and @hh (Thank you both for your input and guidance) I propose the following for next steps on this work:
/cc @BenTheElder @wojtek-t @kubernetes/sig-testing @kubernetes/sig-release |
|
/milestone v1.25 |
|
I have done work on this in my local dev env to configure a Prow Job to run the report automatically. Using pj-on-kind.sh to test in a local env. I reached out to SIG Testing on Slack to find out how to best inject the required GITHUB_AUTH token into the container where the report runs. @BenTheElder, super helpful as ever, let me know that I would need to speak to the github-management team on the specific question of GH Tokens. We have reached out to the them on slack. Relevant docs are here https://github.com/kubernetes/community/tree/master/github-management Additionally, Ben pointed out that I could run this report as a Github Action which I will also look at today from a learning pov. https://docs.github.com/en/actions/learn-github-actions During discussions with @leonardpahlke at KubeCon we both have ambitions to make use of his report to track stats such as Mean Time to Resolve Reported Flakes, Reported Flake Count per Release Cycle, per SIG etc. etc. so as we consume the report we want to encourage the SIG Release Team to suggest stats that the community would find useful to identify resource gaps on the project from the e2e test maintenance POV. I have added this issue to the agenda of the upcoming meeting so as to solicit input from SIG Release (and Release Engineering) and on best course of implementation action (ProwJob vs. Github Action) and also start thinking about analytics we could mine both within a release cycle and across release cycles. |
|
Discussed next steps on this at the SIG release meeting date today, Tuesday May 31, 2022 Thanks to everyone who provided feedback. Ref: SIG Release Meeting Tuesday May 31, 2022 |
|
Next Steps ...
|
|
Another option would be to let the report run over the https://github.com/kubernetes-sigs/testgrid-json-exporter project. |
|
The Kubernetes project currently lacks enough contributors to adequately respond to all issues and PRs. This bot triages issues and PRs according to the following rules:
You can:
Please send feedback to sig-contributor-experience at kubernetes/community. /lifecycle stale |
|
The Kubernetes project currently lacks enough active contributors to adequately respond to all issues and PRs. This bot triages issues and PRs according to the following rules:
You can:
Please send feedback to sig-contributor-experience at kubernetes/community. /lifecycle rotten |
|
The Kubernetes project currently lacks enough active contributors to adequately respond to all issues and PRs. This bot triages issues according to the following rules:
You can:
Please send feedback to sig-contributor-experience at kubernetes/community. /close not-planned |
|
@k8s-triage-robot: Closing this issue, marking it as "Not Planned". In response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
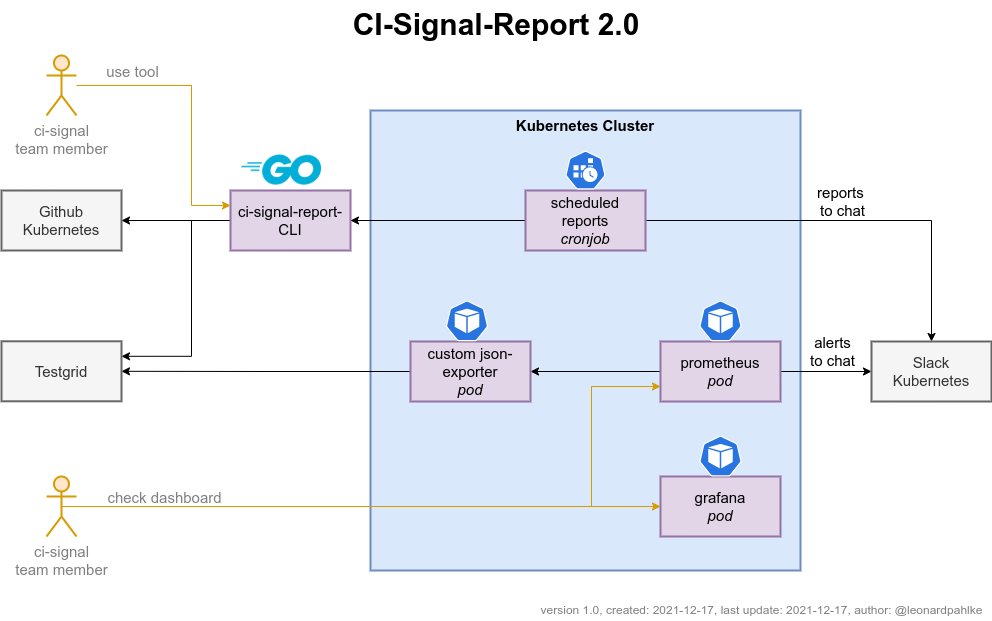
which part of the ci-signal-tool does this effect
Summary: Generate a weekly ci signal report which can be manually shared in slack & k/dev
Current situation
Currently, the weekly ci signal report is generated manually. Some inputs are supplied by this tool. This can be fully automated. See previous ci signal reports for template reference
Desired outcome
The ci sginal report tool should enable creating the entire weekly ci signal report.
Benefits: The preparation of the weekly ci signal report takes some time each week, which could be better used. In addition, establishing a clear structure via the ci signal reporting tool would ensure the quality of the report.
Concerns: The report sometimes contains references to specific events, such as release cuts and specific information about a topic or similar. These must be added dynamically
/kind feature
The text was updated successfully, but these errors were encountered: