-
Notifications
You must be signed in to change notification settings - Fork 1.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add command for signing windows executables with the default code signing certificate #3772
Conversation
|
@devinbileck Could you please verify if the behavior is now as expected for Windows OS? |
|
Posting my results here. I still get the smartscreen dialog, although it does show you as the publisher: As mentioned here:
I am not sure if the EV certificate is worth the hassle, nor am I sure how long it would take to develop reputation with the standard certificate. |
|
I don't feel well equipped to review this PR. @devinbileck could you do a proper review? Anyone else I can ask? |
Besides being more expensive an EV certificate has stronger KYC requirements. I have to have a look how difficult it would be to get one based on the existing code certificate I already have. Regarding reputation it seems you get it e.g. by getting signed applications installed. So I think maybe we could start with the current code signing certificate to see if it would gain enough reputation already after the next round of updates. @devinbileck What do you think? |
Yes, that sounds good to me. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
ACK
I am not able to test with a signing certificate, but when attempting to run the script without it, I encounter the following error and the script still completes.
SignTool Error: No certificates were found that met all the given criteria.
That seems reasonable to me. That way anyone can still run the script to generate an installer without requiring a signing certificate.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
utACK
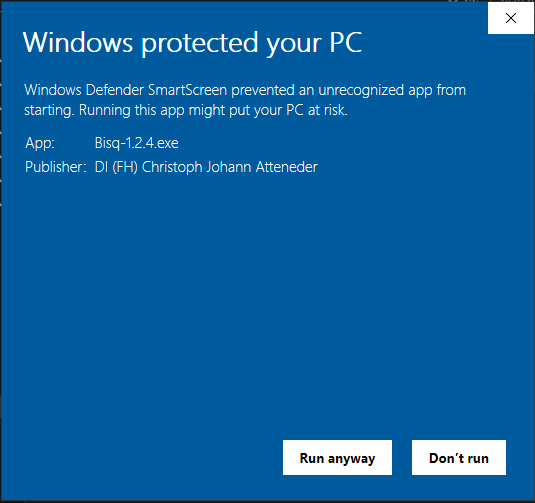
Fixes #1952.
In my role as Bisq desktop maintainer and release manager I applied for a personal code signing certificate for
DI(FH) Christoph Johann Atteneder(yes they wanted all academic titles and names included) at Sectigo (former Comodo). I applied for a code signing certificate which will expire on December 10th 2020.Verification steps
To test the behavior of a signed Windows executable you'll actually need a Windows machine to do so.
For testing purpose I've created a signed version of our Windows installer for v1.2.4.
Executable: https://www.dropbox.com/s/ukrotb5neajgwwu/Bisq-1.2.4.exe?dl=0
Signature: https://www.dropbox.com/s/hasuwvch0lag7wx/Bisq-1.2.4.exe.asc?dl=0