-
-
Notifications
You must be signed in to change notification settings - Fork 698
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Support "allow" block on root, databases and tables, not just queries #811
Comments
|
If the allow block at the database level forbids access this needs to cascade down to the table, query and row levels as well. |
|
I'll need a neat testing pattern for this. |
|
Testing pattern: def test_canned_query_with_custom_metadata(app_client):
response = app_client.get("/fixtures/neighborhood_search?text=town")
assert_permissions_checked(
app_client.ds,
[
"view-instance",
("view-database", "database", "fixtures"),
("view-query", "query", ("fixtures", "neighborhood_search")),
],
) |
|
I'm going to add a |
|
Next step: fix this |
|
The tests in test_permissions.py could check the .json variants and assert that permission checks were carried out too. |
|
I'd like to be able to apply permissions for the ability to run a SQL query - but I'm not sure where the best place for that |
|
Also need to expand the docs on https://datasette.readthedocs.io/en/latest/authentication.html to explain where you can put |
|
Do row-level permissions even make sense? Might be a good idea to remove those until I have a good use-case for them. |
|
I should take these permissions into account when displaying a list of tables or a list of databases (like I do right now when displaying a list of queries). |
|
Per-table permissions is pretty interesting for large installations though - an organization might have hundreds of CSV files imported into Datasette and then allow users to specify which exact users within that organization are allowed to see which CSV. |
Also now using 🔒 to indicate private resources - resources that would not be available to the anonymous user. Refs #811
|
I'm finding myself repeating this pattern a lot: for table in table_counts:
allowed = await self.ds.permission_allowed(
request.scope.get("actor"),
"view-table",
resource_type="table",
resource_identifier=(database, table),
default=True,
)
if not allowed:
continue
private = not await self.ds.permission_allowed(
None,
"view-table",
resource_type="table",
resource_identifier=(database, table),
)I use a similar pattern for lists of databases and lists of queries, and I'll be doing the same thing for lists of SQL views too. An abstraction around this would be useful. Idea: visible, private = await check_visibility(
self.ds, actor, "view-table", "table", (database, table)
) |
|
I really like the padlocks. I should include a screenshot in the documentation that illustrates them. Maybe I should figure out a way to have the https://latest.datasette.io/ demo illustrate both a logged-in and a logged-out state. |
|
Should the padlock show up on tables that are private only because they inherited their privacy from their parent database or even the parent instance? Interesting question. If an instance is private, I'm not sure it makes sense to show padlocks on absolutely everything. Likewise, a list of tables shown on the database table with a padlock next to every single table (when the database itself is private) doesn't seem to add any useful information. I think "Show 🔒 in header on private database page" will resolve this for me. I'll always show the padlock in the header of a database/table page even if that privacy is inherited - but I won't do that for padlocks shown in the list of tables or list of databases. |
Also makes a small change to the /fixtures.json JSON:
"views": ["view_name"]
Is now:
"views": [{"name": "view_name", "private": true}]
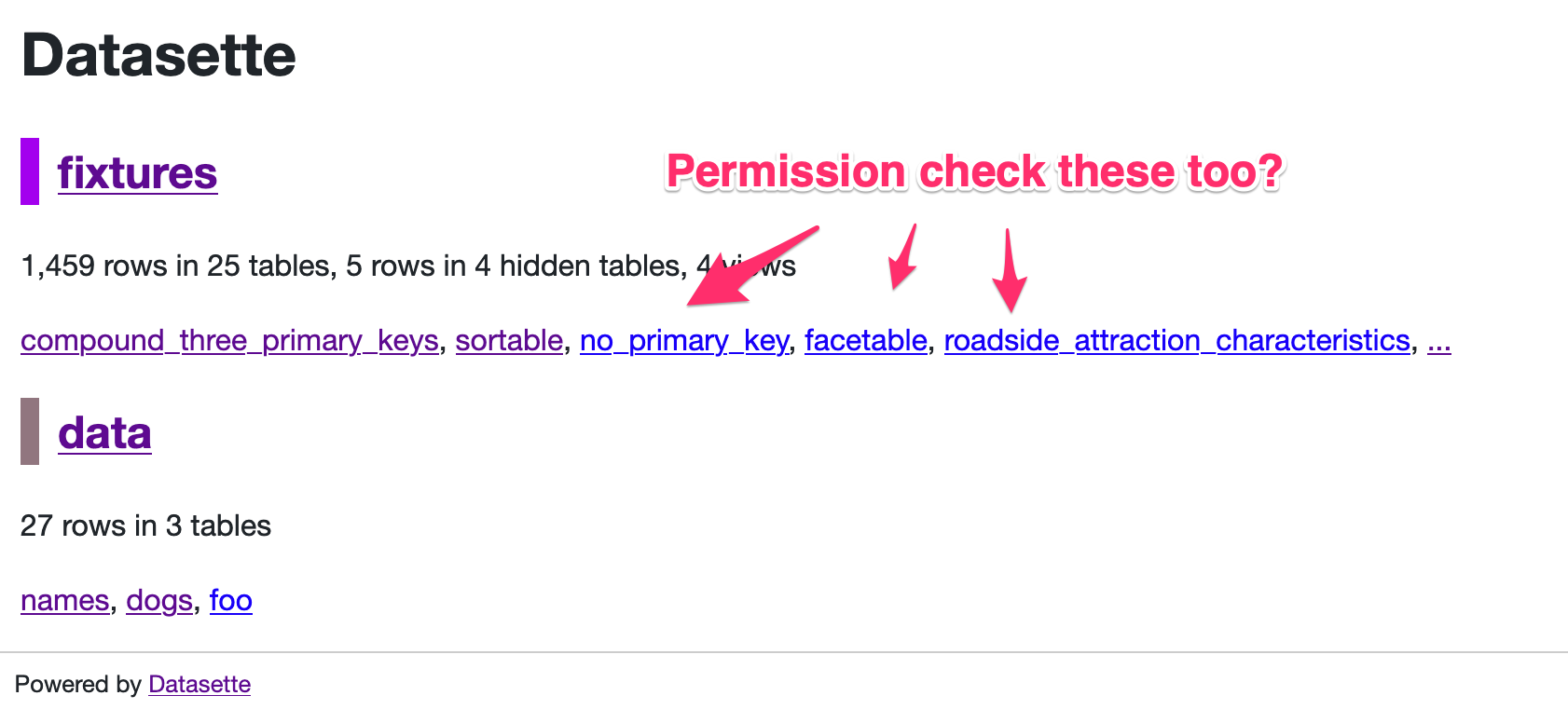


No reason not to expand the "allow" mechanism described here to the root of
metadata.jsonplus to databases and tables.Refs #810 and #800.
{ "databases": { "mydatabase": { "allow": { "id": ["root"] } } } }TODO:
assert_permissions_checked()calls fromtest_html.pytotest_permissions.pyThe text was updated successfully, but these errors were encountered: