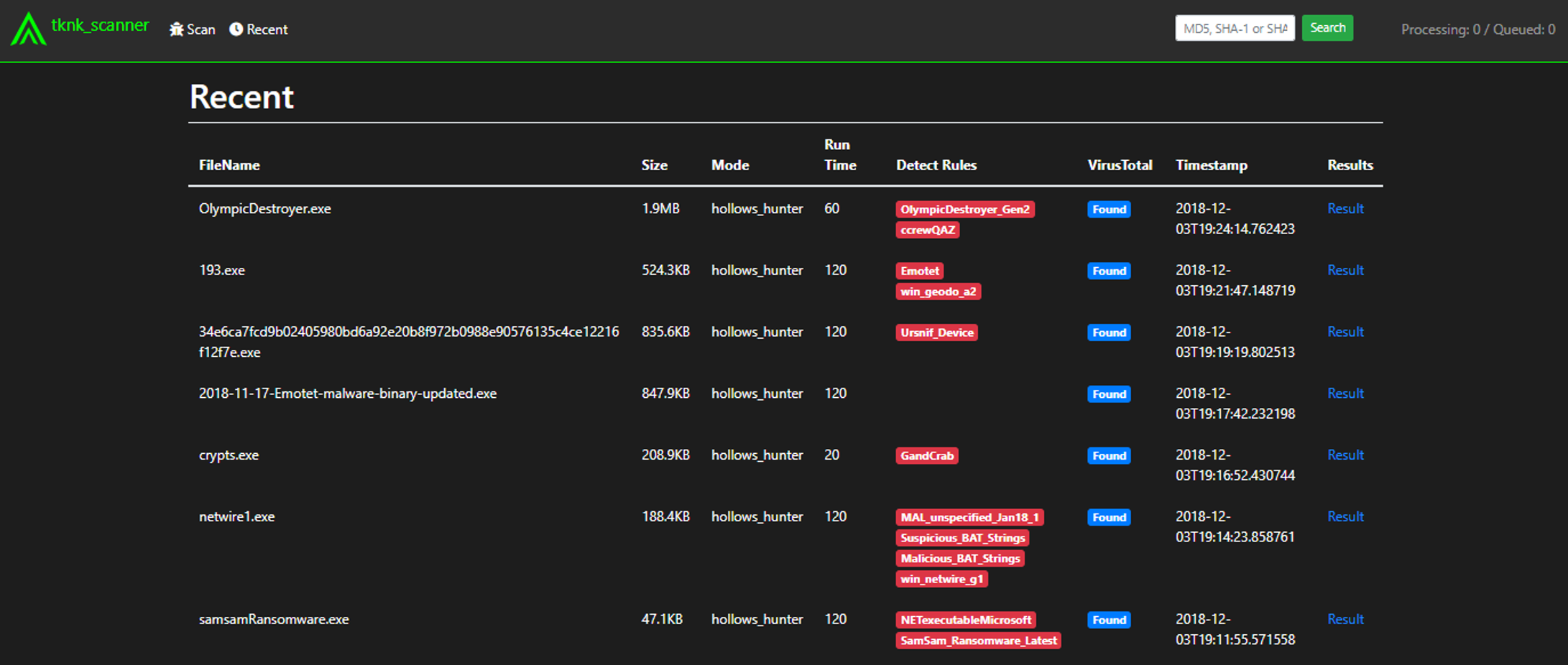
The original code of a malware must be scanned using YARA rules after processing with a debugger (or other means) to account for obfuscated malware binaries. This is a complicated process and requires an extensive malware analysis environment. The tknk_scanner is a community-based integrated malware identification system, which aims to easily identify malware families by automating this process using an integration of open source community-based tools and freeware. The original malware code can be scanned with with your own YARA rules by submitting the malware in PE format to the scanner. tknk_scanner can thus support surface analysis performed by SOC operators, CSIRT members, and malware analysts.
- Automatic identification and classification of malware
- Scan the original code of malware with yara.
- Dumps original code of malware
- You can easily get the original code.
- Community-based
- Integrates multiple Open Source Software and free tools
- User-friendly Web-UI
- Users can submit malware and check scan results using the Web-UI.
- Ubuntu 18.04 (Host OS)
- Windows10 (Guest OS)
- python 3.5 or later
- yara-python 3.7.0
- qemu-kvm
- nginx
- Redis
- MongoDB
- git clone --recursive repository_url
sudo setup/setup.sh- Edit tknk.conf
- vm_name
- Virtual Machine name
- vm_url
- URL of
xmlrpc_server.py - e.g.
http://192.168.122.2:8000/
- URL of
- virus_total
- If VT use, set to 1
- vt_key
- Your VT API KEY
- Download Malware characterization tools
- avclass
$ git submodule update
- Detect It Easy
- Download zip from https://ntinfo.biz/
- Extract zip(Linux Ubuntu 64-bit(x64)) to
tknk_scanner/ - Rename folder name
die
- Download and copy dump tools to
tools/hollows_hunter.exe pe-sieve.dllprocdump.exeScylla.dll - Set yara rules
Save yara rules in "rules" folder. You need to add the rule to index.yar.
- Install Windows on
KVM - Turn off
Windows DefenderandWindows SmartScreen - Install Python 3.6
- Set to the IP address described in
vm_url. - Copy and run
xmlrpc_server.py(Recommend run script as Administrator) - Make snapshot
$ cd frontend/
$ npm install
$ npm run generate
$ mkdir /usr/share/nginx/tknk/
$ sudo cp -rf dist/* /usr/share/nginx/tknk/
$ cd ../
$ sudo cp -f tknk-scanner.nginx.conf /etc/nginx/sites-available/default
$ sudo systemctl restart nginx
$ cd tknk_scanner/
$ ./tknk.py
At another terminal
$ cd tknk_scanner/
$ rq worker
-
File upload
Upload the file to be scanned. -
time
Sets the time to start runing dump tools. The default is 120 seconds. -
mode
- hollows_hunter
Using hollows_hunter. - prodump
Using procdump. - scylla
Using Scylla. - diff(procdump)
Dump the newly created process while running with procdump.
- hollows_hunter
https://www.youtube.com/watch?v=_lXFYIT5Mzc
tknk_scanner is open-sourced software licensed under the MIT License
- Developer
- dump tools
- hollows_hunter (@hasherezade)
- ProcDump (Sysinternals)
- Scylla (NtQuery)
- Malware characterization tools
- AVClass (IMDEA Software Institute)
- Detect it Easy (horsicq)
- Artwork
- Icons made by Freepik from www.flaticon.com is licensed by CC 3.0 BY