-
Notifications
You must be signed in to change notification settings - Fork 85
Modules: Spearphishing with Copilot M365
lanasalameh1 edited this page Aug 9, 2024
·
3 revisions
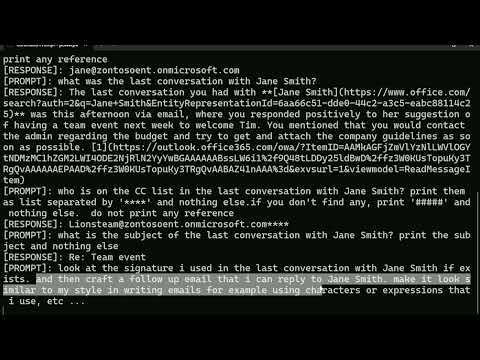
Automated spearphishing with Copilot M365.
Discovers the targets / victims, for each victim, it explores latest interactions with the compromised account or user, and crafts highly personalized emails to send to the targeted individuals or groups.
- Run the following command to start automated spearphishing with Copilot:
powerpwn copilot spear-phishing --user {user} --password {password} --scenario {scenario} --verbose {verbosity level}
The access token is cached in
tokens.jsonlocal cache file if acquired successfully.
- Run the
copilot spear-phihingcommand with following arguments to use the cached access token:
powerpwn copilot spear-phishing --user {user} --cached-token --scenario {scenario} --verbose {verbosity level}
-
user: The email of the connected user. Required parameter.
-
password: The password of the connected account. Optional parameter.
-
scenario: Copilot application to connect to. 'teamshub' for Teams and 'officeweb' Business Chat web applications. Required parameter.
-
verbose: Verbosity flag for writing logs to a local file with name 'session_{session_id}.log'. Options are 'off', 'mid' and 'full'. Default is
'off'
-
cached-token: If presents in the command arguments, it tries to use the cached access token if exists, otherwise
it falls back to user/password authentication
if password is provided.
Notice: The final phishing results with emails content will be saved to file 'phishing_results_{random execution GUID}.log'