-
-
Notifications
You must be signed in to change notification settings - Fork 5.5k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Branch selector disappear immediately (Uncaught EvalError: 'unsafe-eval' is not an allowed) #19851
Comments
|
I know some other users also met the similar problem, I forget the details but in the end it's not a bug. Could you try to:
|
|
Ah, you found it, somehow. (it also match the behavior of the test gitea instance, since there is no CSP there) Maybe not depending on "eval()" code would be a good thing in the future, this does fix the issue in that particular case. |
|
Hmm .... some frameworks need |
eval function is blocked by CSP)
|
@CleyFaye are you also able to post the CSP headers that you are applying? |
|
Yes. I trimmed it down to what seems to be the minimum extra stuff for gitea to operate: Removing either "unsafe-inline" or "unsafe-eval" from |
|
Might be worth searching the dependency code for |
confirming that running Gitea with CSP headers not containing additionally, that practically means all instances (even with CSP configured as tightly as possible to still have working buttons etc.) are vulnerable to XSS in one form or another [1], which doesn't exactly cheer me up. as was (in part) previously mentioned, the solution would be:
OR
while I feel either of the proposed solutions would be greatly improving the security grounding of Gitea as a widely-deployed internet-facing service, I am aware it would require quite some time and energy to evaluate, implement and review. perhaps it is still better than nothing to at least start a discussion. just my two cents. ref: |
|
|
not force but maybe point out the issue, etc.
that is great 🚀
I get that certain mechanisms utilise this extensively (and getting rid of them would be a longer-term effort), however, the issues with those have also been made public [1], [2], [3], such as inline styles enabling a refs: |
Sure, maybe as a start, someone could collect all current uses of
Agree, but it'll be a big refactor to even get inline-styles out of first-party code. For example jQuery |
awesome, that should be possible.
indeed, not to play it down, it for sure will be a big one, but that is to be expected considering not only how extensively those features were being used throughout the codebase but also the course of time (years) over which this type of code was slowly being added. |
|
I'm very sorry but this has to be fixed if gitea want's to remain "best in Class" |
|
Maybe it's more complex than it looks. From the source code of Vue reference: https://stackoverflow.com/questions/68459611/how-to-fix-unsafe-eval-error-with-vue3-for-the-client-side-version , make Vue templates pre-compiled to drop the compiler. And, to be honest, I do not think the CSP unsafe-eval problem is a blocker or harmful: no Gitea frontend code depends or uses it, so it doesn't cause security problem for Gitea at the moment (if there is any security problem, please report). Conclusion: refactor to resolve it fundamentally. |
|
Precompiling Vue templates does sound like the solution and it will also increase performance because we don't need to ship and compile templates at runtime. I'm sure there must be some webpack plugin to make it happen. Maybe like https://stackoverflow.com/a/70665152/808699, but I'm not sure we can completely eliminate the runtime compiler as I recall there are some non-SFC components and those can not be pre-compiled without rewriting them. |
|
One of the challenge is |
|
Yeah, that abomination needs to be rewritten as pure SFC. |
eval function is blocked by CSP)eval function is blocked by CSP, Uncaught EvalError)
eval function is blocked by CSP, Uncaught EvalError)Sadly required by some of the third-party JavaScript frameworks Gitea is using. go-gitea/gitea#19851
Follow: * #23345 The branch/tag selector dropdown mixes jQuery/Fomantic UI/Vue together, it's very diffcult to maintain and causes unfixable a11y problems. It also causes problems like #19851 #21314 #21952 This PR is the first step for the refactoring, move `data-` attributes to JS object and use Vue data as much as possible. The old selector `'.choose.reference .dropdown'` was also wrong, it hits `<div class="choose reference"><svg class="dropdown icon">` and would cause undefined behaviors. I have done some quick tests and it works. After this PR gets merged, I will move the code into a Vue SFC in next PR. 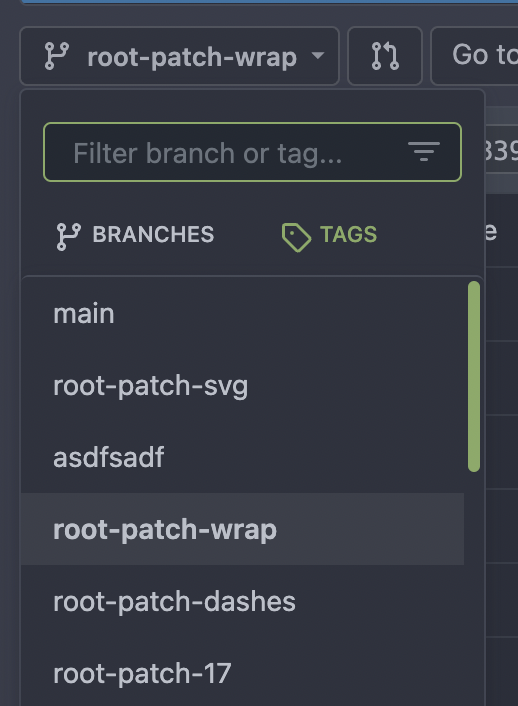 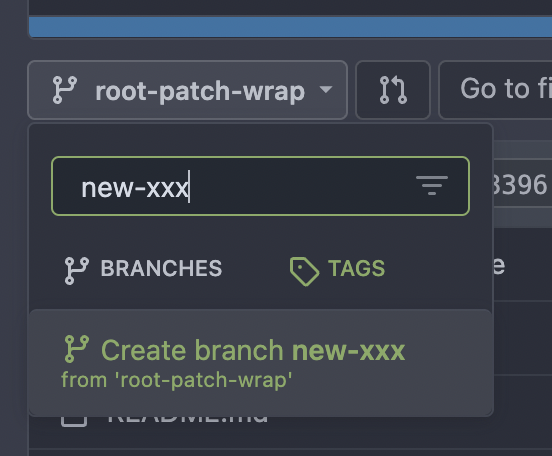 --------- Co-authored-by: techknowlogick <[email protected]>
|
Update: this issue (update: only the 'unsafe-eval' part) will be resolved by: |
Follow #23394 There were many bad smells in old code. This PR only moves the code into Vue SFC, doesn't touch the unrelated logic. update: after 5f23218 , there should be no usage of the vue-rumtime-compiler anymore (hopefully), so I think this PR could close #19851 --------- Co-authored-by: Lunny Xiao <[email protected]>
Description
Hi,
When browsing a repository on gitea, the branch selection widget disappear as soon as the page complete loading.
Disabling JavaScript leave the widget visible.
I'm not sure if any config would be relevant to help diagnose the issue. Although it seems to be fixed in the test instance of gitea, it is currently not available as docker images so the issue persist.
Screenshots
With JavaScript disabled, the widget is visible:

With JavaScript enabled:

Gitea Version
1.16.8 built with GNU Make 4.3, go1.18.2 : bindata, timetzdata, sqlite, sqlite_unlock_notify
Can you reproduce the bug on the Gitea demo site?
No
Operating System
Linux
Browser Version
Chrome 101.0.4951.64
The text was updated successfully, but these errors were encountered: