-
Notifications
You must be signed in to change notification settings - Fork 10.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
IDX40001: Issuer: 'https://tenantname.b2clogin.com/tenantId/v2.0/', does not match any of the valid issuers provided for this application. #51005
Comments
|
Hi @danroth27 , Update 9/29/23:Looks like the problem is with I created a brand new Blazor Server project with this CLI command: Full source code here: But when I changed it to I then wanted to create a new Also Visual Studio Version 17.8.0 Preview 2.0 doesn't present any window to choose Authentication type. So I created a new Full source code here: |
|
Hello I have the same problem, migrating a .NET 7 to .NET 8 RC, using Rider on Mac. Same problem when i use VSCode to start the application. After logging in i get the following message in my API project: Microsoft.IdentityModel.LoggingExtensions.IdentityLoggerAdapter[0] Dieter |
|
@affableashish I'm also facing the same issue |
|
I believe this is a .net 8 specific issue, but I think I have a workaround. Tl;dr - set the IssuerValidator Insecure, but hopefully quite temporary implementation (accepts any issuer): More robust version in the code linked below: AzureAD/microsoft-identity-web#168 (comment) led to |
|
I submitted a PR to fix this at AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet#2361. In the meantime, another workaround is the following to go back to pre-.NET 8 behavior: builder.Services.Configure<OpenIdConnectOptions>(OpenIdConnectDefaults.AuthenticationScheme, options =>
{
options.UseSecurityTokenValidator = true;
});There's a breaking change announcement at aspnet/Announcements#508 that list this as one of the workarounds, but this was not a scenario that should have broken. |
|
@halter73 Thank you! |
…kages to the latest patch release (7.0.3 & 2.15.2) (#51430) # Update the Microsoft.IdentityModel.* and Microsoft.Identity.Web.* packages to the latest patch release (7.0.3 & 2.15.2) Update the reference to the Microsoft.IdentityModel.* and Microsoft.Identity.Web.* packages so that we don't regress AAD authentication scenarios for web apps. ## Description We've hit an issue with AAD authentication in ASP.NET Core web apps, which was resulting in errors during login. This was due to an issue in the IdentityModel package, for which @halter73 has proposed a fix: AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet#2361 The Identity team has approved the fix and has released a new package to NuGet so that we can update our dependency and **avoid the regression in 8.0**. Please note, that this change will have to include the soure-build change as well: dotnet/source-build-externals#228 Fixes #51005 ## Customer Impact Customers who will try to use AAD authentication for their ASP.NET Core web applications in 8.0 will fail to login. ## Regression? - [x] Yes - [ ] No This was technically an existing bug, which was already in the IdentityModel package, however only after a recent change #49542 the issue has surfaced impacting 8.0 apps. ## Risk - [ ] High - [ ] Medium - [x] Low From our point of view this is a dependency update. And the dependency has taken only a targeted fix to avoid the bug, going through all the necessary validation on the AAD side. ## Verification - [x] Manual (required) - [ ] Automated ## Packaging changes reviewed? - [ ] Yes - [ ] No - [x] N/A ---- ## When servicing release/2.1 - [ ] Make necessary changes in eng/PatchConfig.props --------- Co-authored-by: dotnet-maestro[bot] <dotnet-maestro[bot]@users.noreply.github.com> Co-authored-by: Stephen Halter <[email protected]>
[](https://renovatebot.com) This PR contains the following updates: | Package | Change | Age | Adoption | Passing | Confidence | |---|---|---|---|---|---| | [System.IdentityModel.Tokens.Jwt](https://togithub.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet) | `7.0.2` -> `7.0.3` | [](https://docs.renovatebot.com/merge-confidence/) | [](https://docs.renovatebot.com/merge-confidence/) | [](https://docs.renovatebot.com/merge-confidence/) | [](https://docs.renovatebot.com/merge-confidence/) | --- ### Release Notes <details> <summary>AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet (System.IdentityModel.Tokens.Jwt)</summary> ### [`v7.0.3`](https://togithub.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet/blob/HEAD/CHANGELOG.md#703) [Compare Source](https://togithub.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet/compare/7.0.2...7.0.3) \====== ##### Bug Fixes: - Fix errors like the following reported by multiple customers at [dotnet/aspnetcore#51005](https://togithub.com/dotnet/aspnetcore/issues/51005) when they tried to upgrade their app using `AddMicrosoftIdentityWebApp` to .NET 8. See [PR](https://togithub.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet/pull/2361) for details. - Fix compatibility issue with 6x when claims are a bool. See issue [#​2354](https://togithub.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet/issues/2354) for details. </details> --- ### Configuration 📅 **Schedule**: Branch creation - "after 10pm every weekday,every weekend,before 5am every weekday" in timezone Europe/Berlin, Automerge - At any time (no schedule defined). 🚦 **Automerge**: Enabled. ♻ **Rebasing**: Whenever PR becomes conflicted, or you tick the rebase/retry checkbox. 🔕 **Ignore**: Close this PR and you won't be reminded about this update again. --- - [ ] <!-- rebase-check -->If you want to rebase/retry this PR, check this box --- This PR has been generated by [Mend Renovate](https://www.mend.io/free-developer-tools/renovate/). View repository job log [here](https://developer.mend.io/github/orso-co/Orso.Arpa.Api). <!--renovate-debug:eyJjcmVhdGVkSW5WZXIiOiIzNy4xOS4yIiwidXBkYXRlZEluVmVyIjoiMzcuMTkuMiIsInRhcmdldEJyYW5jaCI6ImRldmVsb3AifQ==--> Co-authored-by: renovate[bot] <29139614+renovate[bot]@users.noreply.github.com>




Is there an existing issue for this?
Describe the bug
Experience setting up Auth using Azure AD B2C in a .NET 8 Blazor Web App has been very painful.
The docs are all over the place. Had to piece together information from so many places and still couldn't make it work. 😩
Problem
I've been trying to setup my .NET 8 Blazor Web App (Server side) to connect to Azure AD B2C to log in users and call a secured API.
I have pieced together instructions mostly from here, here and here.
The web app launches, takes me to the login page and lets me enter my credentials:
After I hit "Sign In", it just keeps on spinning and spinning on this url:
And ultimately ends up like this on the redirect url (notice the amount of cookies it tried to set which gets too long and runs into 431 error):
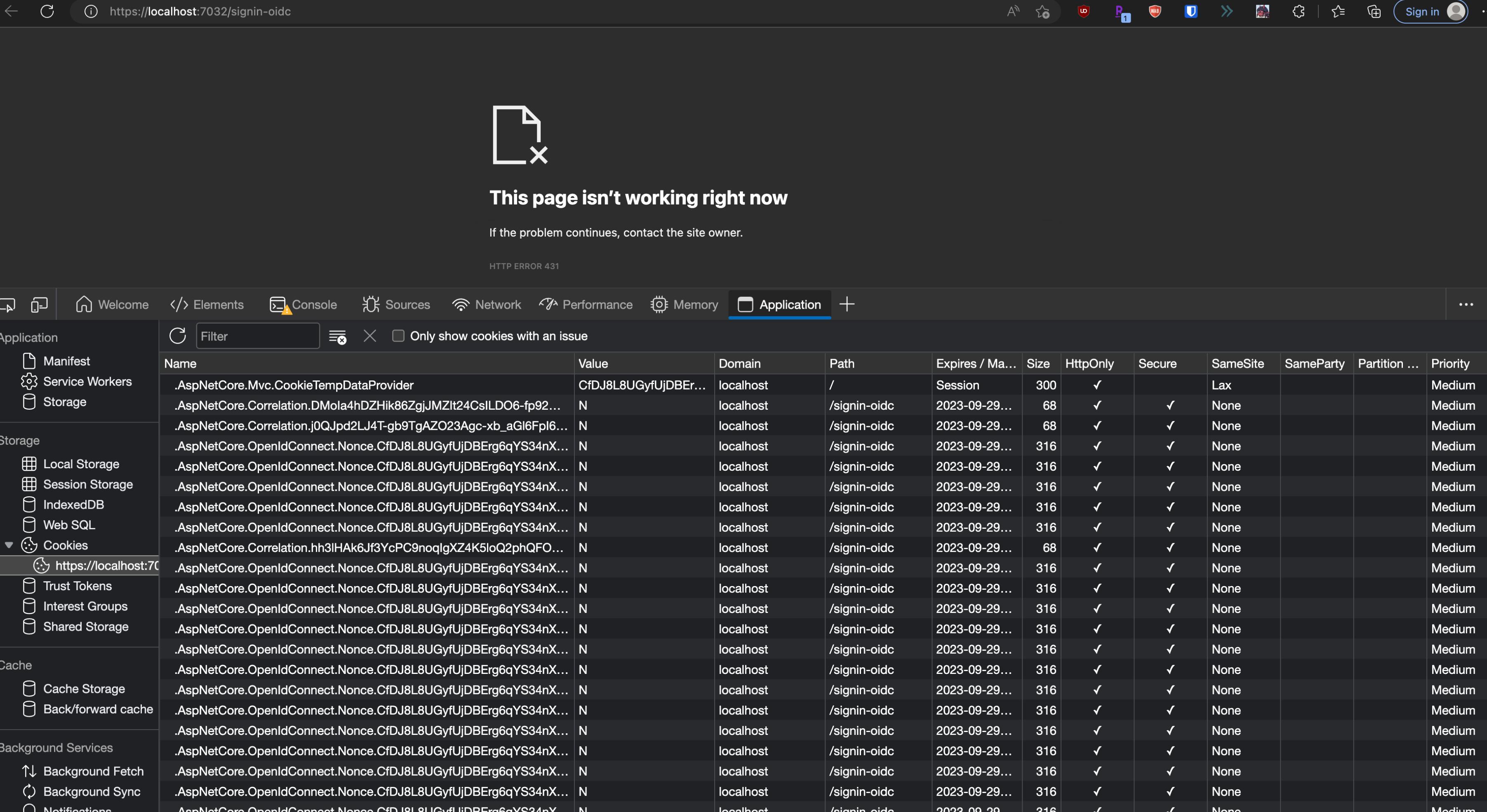
The console of my IDE shows this error:
Microsoft.IdentityModel.Tokens.SecurityTokenInvalidIssuerException: IDX40001: Issuer: 'https://munsonpickles3.b2clogin.com/f6c04159-d728-43cd-8ae1-c1f3793844d5/v2.0/', does not match any of the valid issuers provided for this application.I then checked all the config in my appsettings.json which seems to match what's in the App registration in my AADB2C directory.
The redirect urls are also set correctly:

I ran the flow by pointing the redirect url to
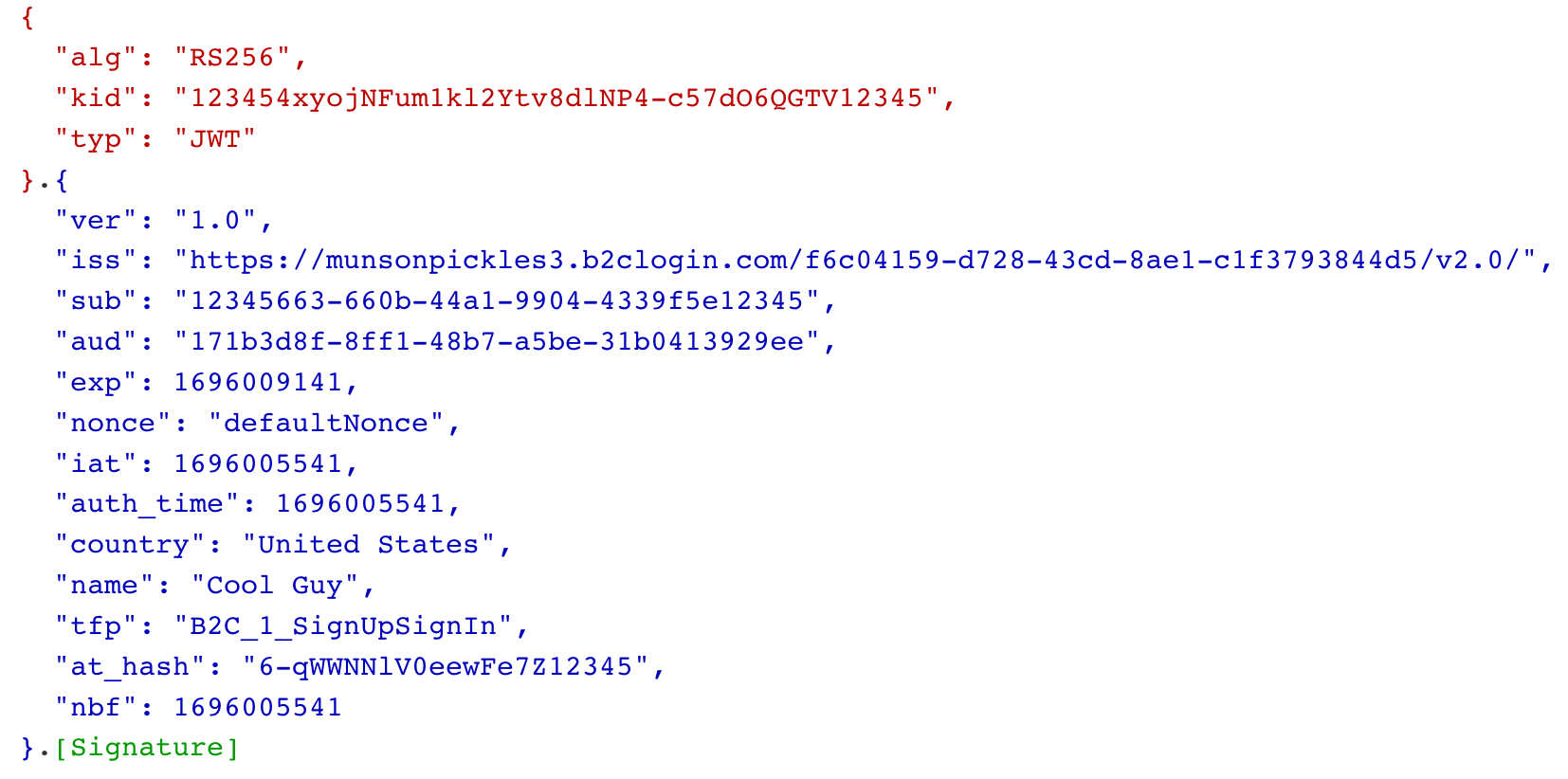
jwt.ms, and looked at the Issuer which is the same one that the app is complaining about:I have followed all the steps by going through all the docs I could find, but after spending 2 days on this, I think I need help.
Please take a look at my full source code to see if you can find something.
Expected Behavior
The app should connect to Azure AD B2C, authenticate the user, get the token, log in the user and redirect to homepage.
Steps To Reproduce
Full Source Code:
https://github.com/affableashish/blazor-server-aadb2c
There are 2 projects: one created on net7.0 and the other on net8.0. The net7.0 project works fine. As for net8.0 project, you can hook up your own AD B2C info in its appsettings.json and give it a try which will fail with the error I've reported here.
Exceptions (if any)
.NET Version
8.0.100-preview.7.23376.3
PII Logs
Anything else?
Also asked a Stack Overflow question about this.
The text was updated successfully, but these errors were encountered: