This repository contains an example Python API that is vulnerable to several different web API attacks.
We will be using docker images and containers to install all the api. This will allow us for easy execution without worrying about setting up Vagrant and other tooling on our environment. We'll leave Vagrant instructions for those who want to also try out that option. You do not need to download this repository.
- Download docker toolbox
- Go through installation steps
- Start up Kitematic
 .
. - In the search box type
mkam/vulnerable-api-demoand click create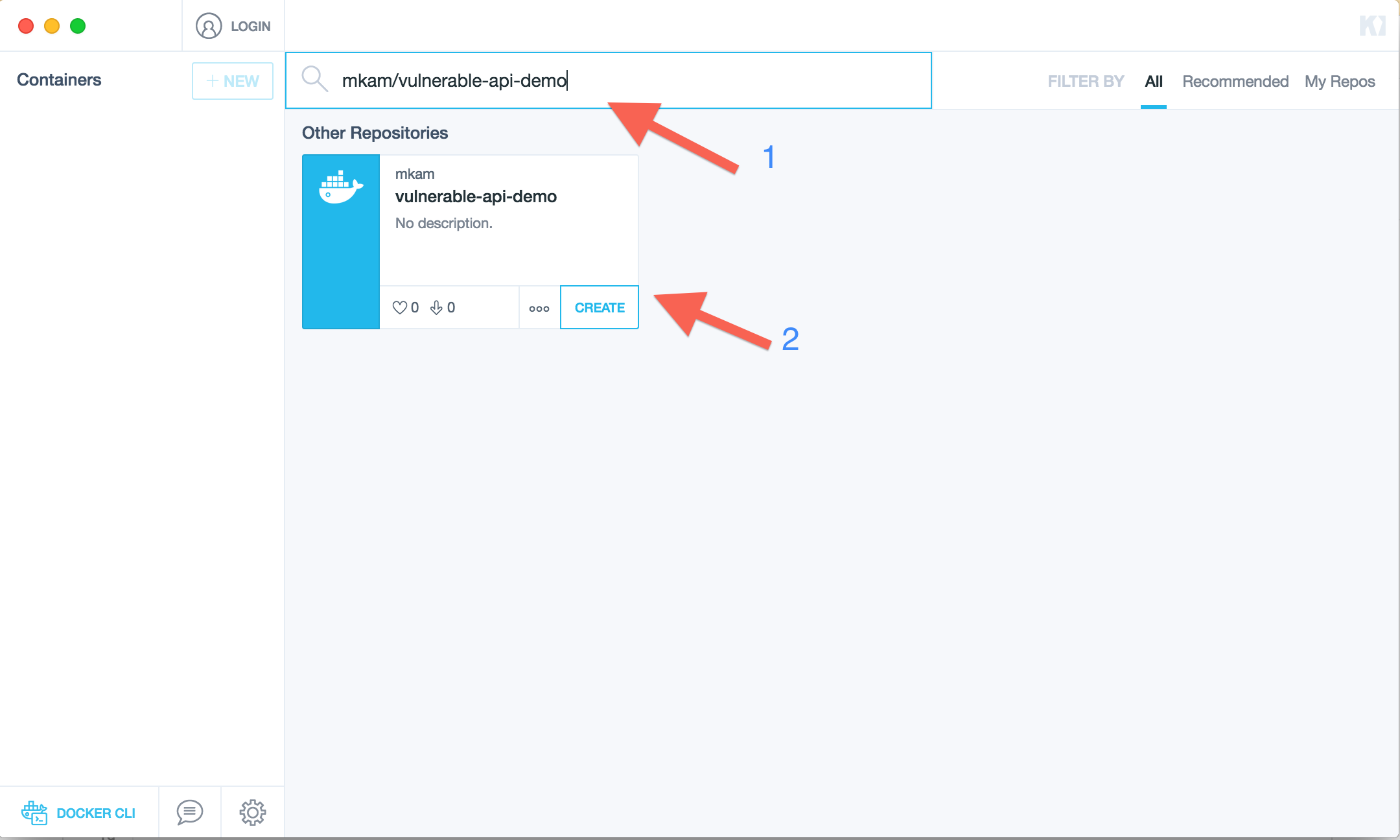 .
. - On right side you will see an IP:PORT access url
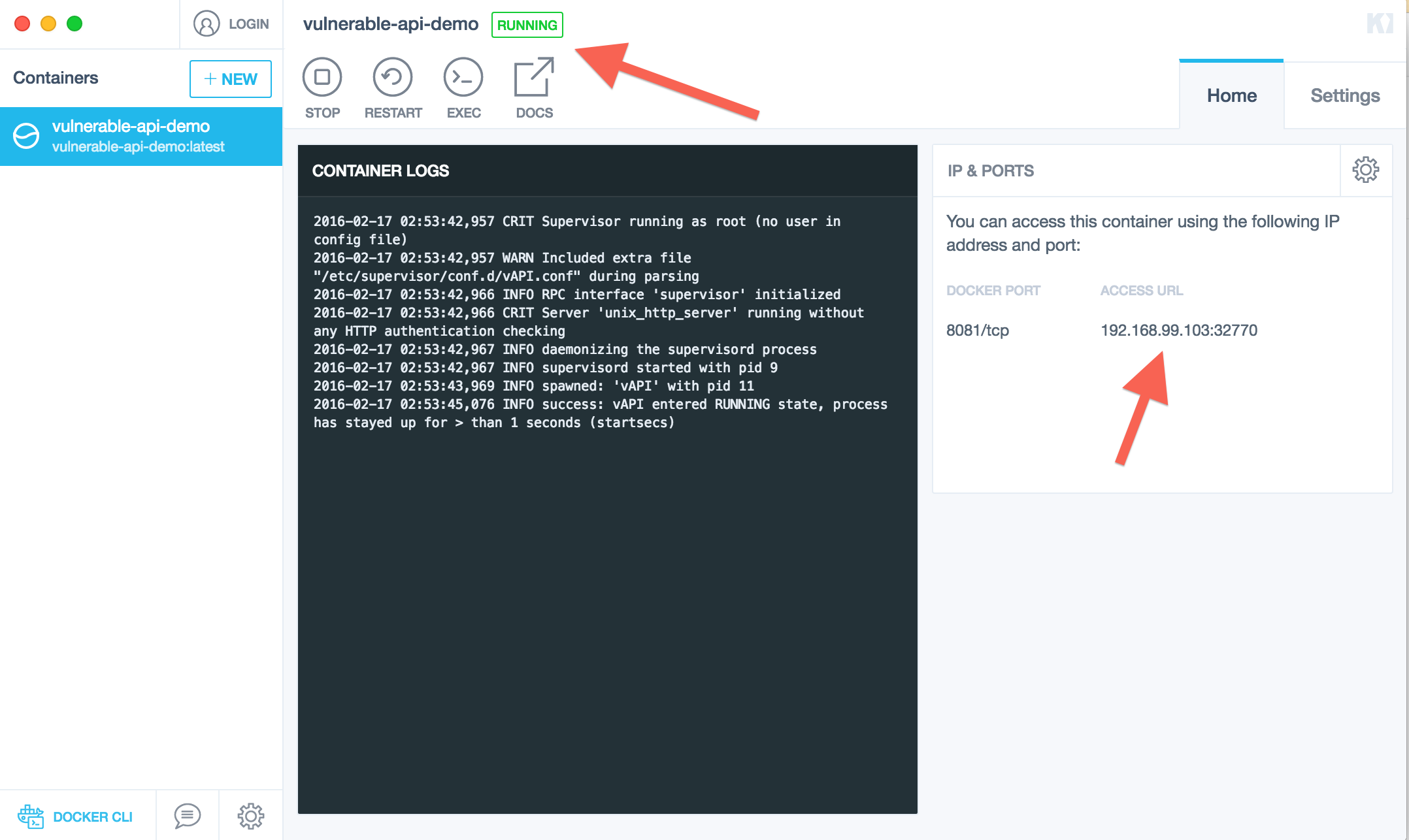 .
. - Copy it and paste into browser to navigate to the api (The error message is what you're supposed to see)
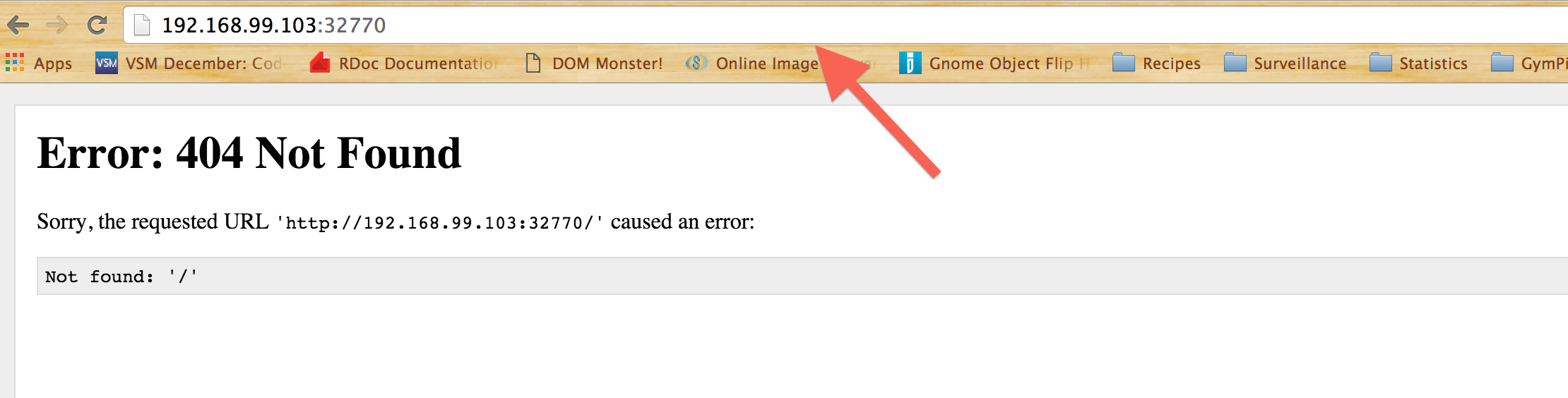 .
.
YOU WILL NEED ADMIN RIGHTS TO INSTALL
- Download docker toolbox
- Go through installation steps
- Start up Kitematic
 .
. - In the search box type
mkam/vulnerable-api-demoand click create .
. - On right side you will see an IP:PORT access url
 .
. - Copy it and paste into browser to navigate to the api (The error message is what you're supposed to see)
 .
.
- Install docker engine and docker client on docker website
- Run
docker run -tid -p 8081:8081 --name api mkam/vulnerable-api-demo - You can now test your api
curl localhost:8081 -v
Ansible - https://www.ansible.com/ Vagrant - https://www.vagrantup.com/
Update vulnerable-api/ansible/roles/api/tasks/app.yaml as follows
- Replace vagrant user with a user with sudo privileges in these two sections.
- name: Stop supervisord
shell: killall supervisord
args:
sudo: yes
sudo_user: vagrant
- name: Start supervisord
shell: supervisord -c /etc/supervisor/supervisord.conf
args:
sudo: yes
sudo_user: vagrant
Run ansible-playbook
ansible-playbook -i "localhost," -c local vulnerable-api/ansible/main.yml
The example API can be accessed on the system at port 8081.
vAPI is an API written specifically to illustrate common API vulnerabilities.
vAPI is implemented using the Bottle Python Framework and consists of a user database and a token database.
- Request token from /tokens
- Returns an auth token
- Returns expiration date of auth token
- Returns a user id
- Request user record from /user/<user_id>
- Requires the auth token
- Returns the user record for the user specfied, provided the auth token is not expired and is valid for the user id specified
- Each user can only access their own record
Included with install
| Username | Password |
|---|---|
| user{1-9} | pass{1-9} |
| admin1 | pass1 |
SYSTEM_IP:8081
Request an Auth Token for a user
- Accept: application/json
- Content-Type: application/json
- username (string) - Name of user requesting token
- password (string) – Password of user requesting a token
- token
- expires (string) – The Auth Token expiration date/time
- token - id (string) – Auth Token
- user - id (string) – Unique user ID
- name (string) – Username
- 200 OK - Request completed successfullyi
POST /tokens HTTP/1.1
Accept: application/json
Content-Length: 36
Content-Type: application/json
Host: 192.168.13.37:8081
{"auth":
{"passwordCredentials":
{"username": "USER_NAME",
"password":"PASSWORD"}
}
}
HTTP/1.0 200 OK
Date: Tue, 07 Jul 2015 15:34:01 GMT
Server: WSGIServer/0.1 Python/2.7.6
Content-Type: text/html; charset=UTF-8
{
"access":
{
"token":
{
"expires": "Tue Jul 7 15:39:01 2015",
"id": "AUTH_TOKEN"
},
"user":
{
"id": 10,
"name": "USER_NAME"
}
}
}
Retrieve the user's entry in the user database
- Accept: application/json
- Content-Type: application/json
- X-Auth-Token: <TOKEN_ID> (from /tokens POST)
- None
- User
- id (string) – Unique user ID
- name (string) – Username
- password (string) – Password
- 200 OK - Request completed successfully
GET /user/1 HTTP/1.1
Host: 192.168.13.37:8081
X-Auth-Token: AUTH_TOKEN
Content-type: application/json
Accept: text/plain
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Length: 0
HTTP/1.0 200 OK
Date: Mon, 06 Jul 2015 22:08:56 GMT
Server: WSGIServer/0.1 Python/2.7.9
Content-Length: 73
Content-Type: application/json
{
"response":
{
"user":
{
"password": "PASSWORD",
"id": USER_ID,
"name": "USER_NAME"
}
}
}
Vulnerability Categories Include:
- Transport Layer Security
- User enumeration
- Information exposure through server headers
- Authentication bypass
- User input validation
- SQL injection
- Error handling
- Session management
- Encryption
- AuthN bypass