-
-
Notifications
You must be signed in to change notification settings - Fork 345
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Enable tls 1.3 by default #783
Comments
|
Hello, I believe you can close this issue. Because we already talking about in this one (n°768). Kind regards. PS : At least thank you @Techguyprivate for the confirmation. Another reason ?
|
|
Hi, just raising security.tls.version.max to 4 will not be enough, as the nss libs in Waterfox are way too old and only support a draft version. I updated the tree to current libs to be able to connect to tlsv1.3 final sites. b. |
From the postscript at https://redd.it/818z1k:
|
From The Waterfox Blog | Waterfox 56.2.6 Release:
Also https://www.reddit.com/r/waterfox/comments/a7f5hz/-/ecj0hms/?context=1 |
|
Accessing https://tls13.crypto.mozilla.org/ is still not possible, alas. |
|
about:config?filter=security.tls.version.max – shows That, with Waterfox 56.2.6 on FreeBSD-CURRENT, Mozilla's NSS TLS 1.3 Demo is reached; and Qualys SSL Labs - Projects / SSL Client Test uses the word experimental:
|
|
Qualys SSL Client Test confirms 1.3 is supported with These tests fail as well on my end so far: |
|
For encrypted SNI, I think the feature will need to be ported over. |
|
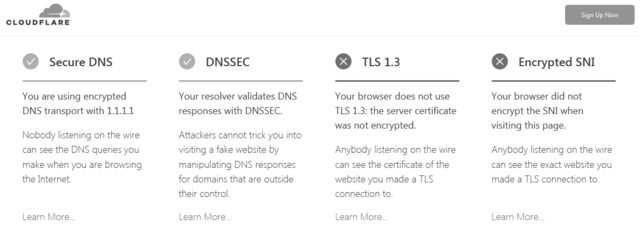
@mparnelldmp, don’t bother with encrypted SNI, the 3rd column of that Cloudflare page is what relevant. |
I get:
– and (side note) the can be blocked by Malwarebytes due to possible suspicious activity
|
|
In Reddit we have a report,
Does any other user of 56.2.6 find this problem – TLS 1.3 not supported? |
|
Out of iterest I just tried the above mozilla test page in the Chromium Web Engine (Vivaldi Browser and QtWebEngine via Falkon Browser), both failed with an SSL exception. Only curl and wget was able to understand TLS 1.3. So Firefox Quantum is the only browser who understands TLS 1.3 if I'm not wrong. 🤔 EDIT: Safari Apple WebKit also works with TLS 1.3 (GNOME Epiphany Web). |
|
Cross reference https://www.reddit.com/comments/9ihvgq/-/ef1jzdl/ |
I also see this. I think #783 (comment) is still the case - currently Waterfox uses NSS 3.34, but full TLS 1.3 support requires at least NSS 3.39. |
|
Waterfox supports TLS 1.3 draft 18 but it's too old. NSS 3.39 or later is required to support the final version of TLS 1.3 as stated above. |
Yeah, I'm still good, it seems (albeit on an unsupported OS) with a locally-built installation: Test pages aside … in simple terms, please, what are the possible/likely ill effects when Waterfox with inferior NSS 3.34 visits a production site that requires (or benefits from) TLS 1.3? Does anyone have an example URL handy? TIA |
https://tls13.crypto.mozilla.org/From #783 (comment):
On FreeBSD-CURRENT I get the page OK with Firefox, surf, Waterfox and Web. No go in Chromium, Falkon, Iridium or SeaMonkey. I might try building SeaMonkey with NSS 3.41.1, but not Chromium or Iridium (Chromium-based browsers are excruciatingly slow to build). |
This also happens at https://tls13.1d.pw/ with Waterfox 56.2.6 using NSS 3.42. |
NB
We're at 56.2.7. Not yet 56.3. |
That's because it requires bug 1430268 (see the Mozregression results below).
|
|
I noticed if I set security.tls.version.min to 4 then check for updates the browser will crash. (Win10x64) |
|
@sheddup can you raise a separate issue for that? Thanks. |
|
Hi, thank you for the explanation @bernhy and sorry for my late reply (I had forgot and I was absent for a long time). |
|
TLS 1.3 will remain disabled by default for v56. v68 has it enabled by default. AFAIK, TLS 1.2 with a decent cipher is still considered secure, there's no point forcing early adoption of a critical piece of software that needs careful implementation. |
|
@MrAlex94 We can't control what TLS version sites decide to force. What reason is there not to implement TLS 1.3 in Waterfox? |
|
@Techguyprivate After 2 years, your dream come true 😄 |
Describe the bug
A clear and concise description of what the bug is.
Tls 1.3 final has been published. Is it possible to enable it by default in waterfox. I have changed security.tls.version.max; to 4, yet no tls 1.3.
To Reproduce
Steps to reproduce the behavior:
**Desktop (please complete the following information):
The text was updated successfully, but these errors were encountered: