Releases: hasherezade/pe-sieve
Releases · hasherezade/pe-sieve
v0.3.0
FEATURE
- supported force-read of inaccessible pages (
PAGE_NOACCESS) when running in the reflection mode (/refl):- automatic if the inaccessible page is within the PE module
- on-demand if the inaccessible page is somewhere else in the workingset (depending on the selected
/datamode)
- added more options for scanning non-executable pages (
/data) - added one more mode of IAT hooks scan (
/iat), allowing to filter out hooks that lead to any system DLL - in hook resolving function: recognize and parse one more jump type
- in shellcode detection: added one more pattern
BUGFIX
- Fixed error in printing JSON reports of some of the scan types (missing headers)
REFACT
- refactoring and optimization of the function resolving hooks
- removed not needed flags for process reflection creation (optimization)
See also HollowsHunter: https://github.com/hasherezade/hollows_hunter/releases/tag/v0.3.0
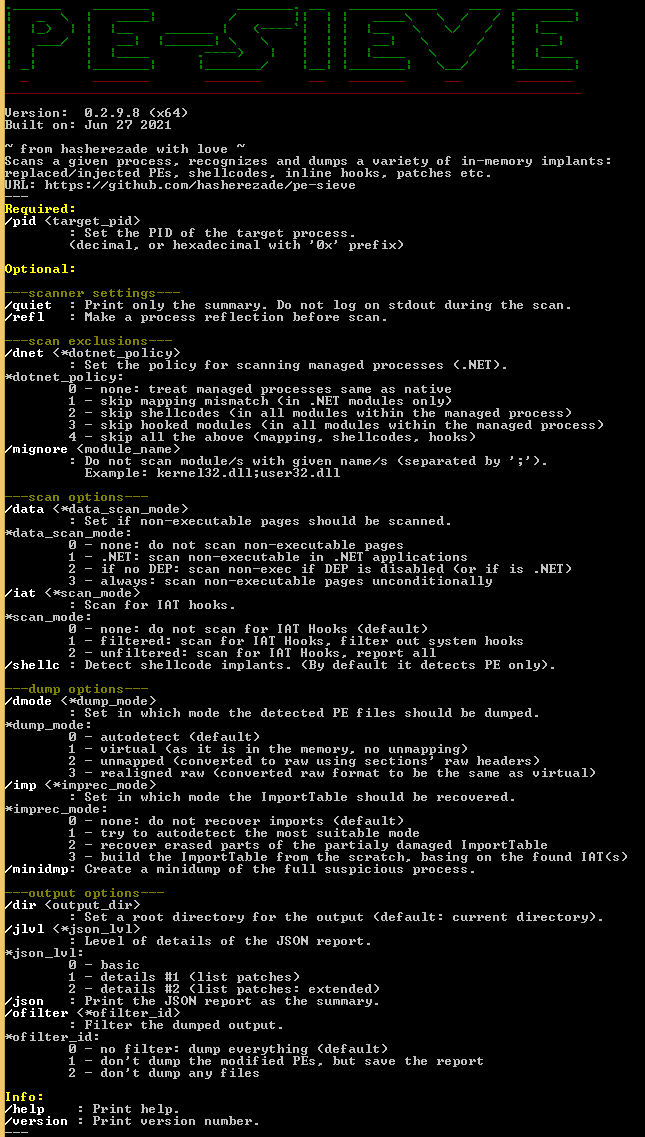
v0.2.9.8
FEATURE
- added a new pattern for detecting 64-bit shellcodes
- added return codes informing about the result of the run
- removed unused parameter :
/mfilter - in JSON: added an indicator if the replaced module was linked to the PEB
BUGFIX
- Fixed error in dumping some of the PEs (issue caused by the invalid ImageSize calculated: Issue #85)
v0.2.9.6
v0.2.9.5
FEATURE
- Improved parameters accessibility: grouped into more categories, sorted.
- Display hints for misspelled parameters
- Added parameter
jlvlallowing to regulate the level of details included in the JSON report. Allow to list hooks/patches in thescan_report. - Improved hook parsing: identify hooks created by replacing the target of existing JMP/CALL
BUGFIX
- Improved reading remote memory (fixed a bug that was causing PE-sieve to stuck in some cases of reading inaccessible memory)
- Do not include initial protection in the check of memory access rights
v0.2.9
FEATURE
- In DLL: use
__cdeclcalling convention (instead of__stdcall) - In case if scanning data is enabled (
/dataparameter) scan for hooks also the sections that are marked as non-executable (if they contain code patterns) - Added a count of sections scanned for patches to the report
BUGFIX
- Fixed a bug in detecting a section with Entry Point (affecting unpacking of some packers, such as ASPack - Issue #73 )
- Fixed bug in libPEconv: do not treat empty relocation blocks as invalid
REFACT
- Some internal cleanup and refactoring
v0.2.8.6
v0.2.8.5
BUGFIX
- Fixed broken detection of ASProtect ( Issue #66 )
- Fixed broken parsing of a hexadecimal PID ( Issue #65 )
- Fixed errors on code scan (caused by invalid relocation table check)
- Do not assume that the section 0 is always executable
- Fixed bug in scanning 64bit modules by a 32bit scanner
FEATURE
- Added one more pattern to detect 64 bit code
REFACT
- Refactored identifying executable sections
v0.2.8.3
BUGFIX
- Fixed hanging during the IAT scan of some PEs
- Fixed error in converting paths from the
/Device/format - Fixed not listing results of the mapping scan in the summary
FEATURE
- added one more .NET policy (in
/dnetparameter) - In the summary: changed
detachedtounreachable_file
v0.2.8
FEATURE
- Detailed info about a single parameter can be requested by:
/<parameter> ? - New modes in the
/dataparameter - New parameter
/dnetallowing to enable treating .NET modules differently than native ones - Report about PE implants and shellcode implants separately
- Added information in the report: process bitness, is process managed (vs native)
- Minor changes in the API:
PEsieve_versionimplemented as a constant - Allow for partial scanning of 64 bit processes by a 32 bit scanner
BUGFIX
- If the parameter
/reflchosen, the process reflection should be used for both scan and dump - Fixed switching back to the original console color after printing in color (improved look on Powershell console)
- Fixed recognizing if the PE in the memory is in raw or virtual mode (it was giving invalid results for some payloads)
- Fixed broken parameter
/mfilter
REFACT
- Refactored parsing of the parameters
- Internal refactoring and cleanup of the scanner
v0.2.7.1
FEATURE
- Scan virtual caves
BUGFIX
- Fixed
/mginoreoption (filtering out selected modules from the scan) - Fixed wrong calculation of a patch size