-
Notifications
You must be signed in to change notification settings - Fork 523
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
FYI: CanvasBlocker can be detected by sites #174
Comments
|
@zymase wrote:
@Gitoffthelawn wrote:
@zymase wrote:
|
|
I don't know that other addon. If it has a "fake readout" functionality it's possibly detectable too. If it only blocks canvas readout then that's detectable anyway. This test is specifically for CanvasBlocker. |
|
I'll echo my comment on Ghacks 👍
At this point I remain uncertain on what is the best option for managing Canvas tracking. |
|
CB blocks the Javascript API + has an option for spoofing.
CB on default uses spoofing as default, but I use it on block mode. CB alone (block mode) isn't a good option, you should find some combo as this one. Otherwise, if you go with the spoofing option (on either CB or CD), you should check how much reliable are those spoofing methods. Altough spoofing sounds better to me, there are some issues to consider. |
|
As far as I understand CB, when choosing CB with Block Mode=fake readout API the process is not that of blocking, literately. CB has several modes (see https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/), and,
Moreover, as I mentioned above, CD didn't notify the active Canvas on Google Maps ... |
|
If it didn't notify, maybe the site has bypassed CD. As Gorhill said on my last link above, these specific addons face many workarounds as counter actions by site owners and developers. I don't know this spoofing reliability: does it spoof various browsers based on your OS? |
|
Well, the site mentioned above doesn't bypass CB ... and CB did not block the canvas (with Block Mode=fake readout API ) but spoofed it in fact, as far as I understand it. I even believe Google Maps just wouldn't run correctly with Canvas blocked. |
|
Gmaps needs the Canvas API to be working correctly. Maybe CB works in a clever way, by spoofing a readout API response that doesn't break Gmaps? better ask @kkapsner |
|
I've tested Google Maps (in fact the true Canvas requirement is Google Street View) with CB's BlockMode=Block Readout API and Google Street View failed (black screen). Now, I read at https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/reviews/890823/ the developer of CB answering this:
So if Goofle Maps/Street View runs with CB/Block Mode=fake readout API it's maybe, as Atavic mentioned it, because that mode is bypassed by Google. In fact when a Canvas blocker/defender doesn't break a Canvas page it is either because it's efficient either because the page bypassed it. This is cruel. |
|
@Atavic wrote,
That's what I had in mind, a hope rather than a certitude, because of above mentioned. All this brain storming for the sole purpose of trying to defeat Web tracking.... |
|
With CanvasBlocker / Block Mode=fake readout API , testing on; 1- https://browserleaks.com/canvas -> Canvas signature different with every page reload 2-https://browserleaks.com/proxy -> HTML5 Canvas Protection detected, as well as with the CanvasBlocker tester page ... PAUSE |
|
This particular fingerprinting isn't so widely used and most of the sites using it call a Javacript file hosted by More here. |
I did mention,
When the test is first performed HTML5 Canvas Protection is not detected, |
|
^^I have |
|
But the link provided by @earthlng gives me |
|
@crssi ,
Tested again, Block mode = fake readout API This is mystery. Of course, as you, earthlng's link to CanvasBlocker detection test proves CB detected. Reminds me my teen-age years, wondering if she loved me or not :) |
|
To bring a little bit insight to the question if the canvas protection is detected or not: this protection detection is performed on a one pixel canvas. CB adds exactly one bit of entropy to one pixel. Therefor it's 50% that the pixel is not altered and therefore the detection does not work. I will update my detection test to include this tests. |
|
@kkapsner to the rescue... nice to have you here. :) |
|
@kkapsner hi and thanks for chiming in here :)
"this protection detection" - which one? https://browserleaks.com/proxy ?
I hope you don't mind that I copied your test file and hosted it on my repo to make it accessible online. |
|
Yes - the one from browserleaks. I don't mind you copying it. But you're right having them online available ist better: http://kkapsner.github.io/CanvasBlocker/test/detectionTest.html |
|
@zymase Seems like the test page compares the results:
Test page stores your fingerprint signature (for the first time).
Test page stores a new signature, compares the results and the only value that has changed raises the detection. |
|
@Atavic that's what I had in mind initially. I just checked, as before with Block Mode = fake readout API BUT with this time Random Number generator = persistent => same sig and indeed Canvas Protection not detected, initially and on page reload. Makes me realize I mistaked above when I answered to crssi:
In fact it is: What likely happened is that I had forgotten to clear the site's cache/cookie. |
|
@kkapsner Great, thanks, I updated the link in my first comment and removed the now outdated detection test from my repo. |
@kkapsner already explained that - it's pure RNG ie sometimes CB happens to change the value the code is looking at and other times not. 50-50 chance This is the code the page uses, which shows that they only look at the "red" value (RGBA) of the 1st pixel and if that changes it knows that the readout was tampered with function tbb_canvas() {
try {
var a = document.createElement('canvas').getContext('2d');
return a.fillStyle = 'rgb(3,3,7)',
a.fillRect(0, 0, 1, 1),
a.fill(),
3 !== a.getImageData(0, 0, 1, 1).data[0]
} catch (a) {
return !1
}
}They could easily make this a 100% reliable test if they look at all 4 values for that pixel |
|
@kkapsner how much identifiable bits can a single pixel really give? Not much I reckon. I assume most sites that use canvas fingerprinting have to use a larger canvas than that. You could maybe detect if a site only wants ImageData for width=1 && height=1 and not tamper with that. That would also have the benefit of always returning correct and un-tampered values for any color pickers out there. Like? xD |
https://web.archive.org/web/20141228070123/http://webcookies.org:80/canvas-fingerprinting/ https://browserleaks.com/canvas#how-does-it-work |
|
I already included a new parameter for the next version to specify a minimal canvas size for faking (defaults to 1 so 1 pixel canvases are not faked). The double readout detection can be circumvented by using the persistent random number generator. |
Nice, but I just realized that nothing really stops a site from loading a larger canvas pixel by pixel and putting the array together that way, right? Damn! Maybe make the minimal canvas size optional?
oh nice, I was wondering if that's what that is for. How does that work - does it keep the same data across all windows and tabs for the whole session, and unless "stored" will only change with the next FF startup? |
|
I have to correct me: every pixel has four bits of entropy - one for every channel. |
|
I changed the way the max readout size works: in the new version (unfortunatelly I have no release date or schedule as I'm waiting for Mozilla to provide an API so I can feed the settings to the tabs before the scripts of the web page run - hoorray WebExtensions!!!) it's only dependent on the canvas size and not on the readout size. Same for the min size - so a large canvas can not be put together by single pixels. Yes - the persistent rng keeps the same data across all windows and tabs for the whole session. If you tick the "store persistent data" it will be written to your settings and reloaded after shutdown. |
|
hoorray WebExtensions!!! indeed - good stuff 🤦♂️
Why not? I don't see how you could possibly prevent that, assuming you don't simply ignore how much data a site requested.
Thanks for confirming. I also noticed on the browserleaks testpage that if you look at the image details, the file size and number of colors barely changes with "persistent" but with "non persistent" it changes a lot. So that probably stands out a lot. The file size with CB disabled or CB "persistent" is around 2kb and with non persistent it's upwards of 7kb, while the # of colors changes from around 70 to 300+. That and the fact that if your IP doesn't change neither should the canvas fingerprint (IMO), I think making "persistent" the default setting would probably be better. I think even in Tor Browser "persistent" would be preferable. Thanks for creating and maintaining this great addon btw! |
|
@Gitoffthelawn wrote:
That's weird because when I tested it, it was detected by both length and name. Not only that but its exposed function also had 2 additional variables that neither the original function nor CB's function has. |
@earthlng are we referring to the same test? But running Canvas Defender and testing on https://browserleaks.com/proxy showed that a Canvas Blocker was indeed detected. |
yes, I tested it yesterday and CD was detected. Idk what to tell you, no idea whats causing that. |
I assume you mean on https://kkapsner.github.io/CanvasBlocker/test/detectionTest.html I disabled CB and installed CD (again) this morning to test CD on https://browserleaks.com/proxy and Canvas Blocker was detected. I did not test this time on https://kkapsner.github.io/CanvasBlocker/test/detectionTest.html because previous testing there showed CD was not detected. If you wish I may test again CD on https://kkapsner.github.io/CanvasBlocker/test/detectionTest.html |
|
https://kkapsner.github.io/CanvasBlocker/test/detectionTest.html |
|
I've removed the BlockCanvas Firefox add-on and wont be using Block Defender either. Why? Seems to me this blocking is pertinent when the scenario is using multiple identities and/or several browsers. If I understand correctly what is explicitly explained by the developer of Block Defender :
I get to consider that blocking Canvas fingerprinting has no real advantage when other defenses aren't included, in other words don't block the fingerprinting unless you change identity. I'm not concerned. |
|
@zymase "multiple identities" can also mean different IPs. If your IP changes but you still produce the same (perhaps unique) canvas fingerprint, that's something you may not want. |
Yeah, that's how I get it. My feeling is that Canvas Blocking fills the gap left when the scheme is that of multiples identities or TOR, VPN : the user hides but is recognized by a Canvas fingerprinting : too stupid, all that work to finally get spotted with a Canvas! Otherwise, a simple traveler like me ends up being spotted as someone who breaks Canvas fingerprinting without the benefit of not being recognized ... Again, nothing is definitive. I try to learn and if I understand that I'd be mistaking that I'd reconsider Canvas fingerprinting when applied for my Web sessions. |
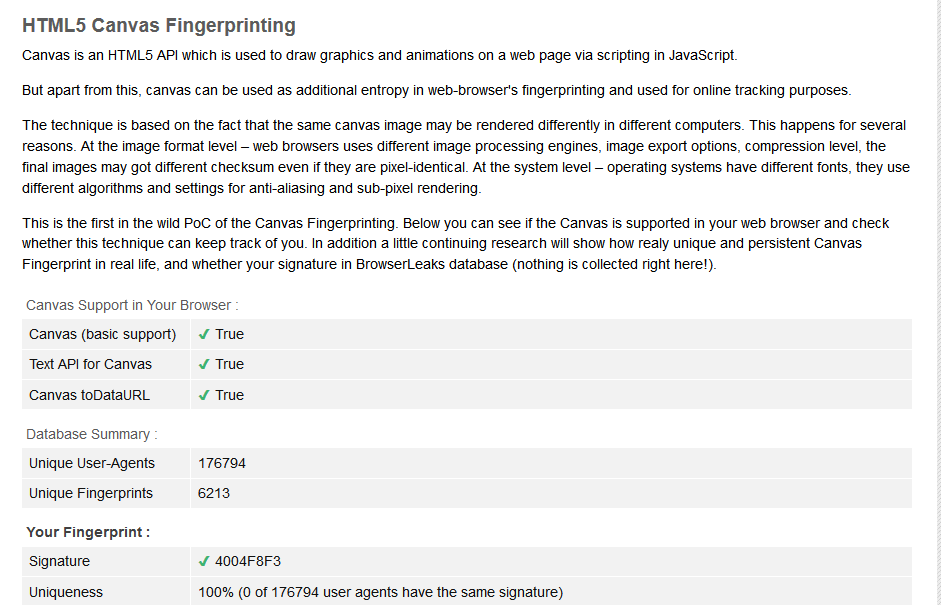

moved from #12
kkapsner/CanvasBlocker#114 (comment)
Detection Test: https://kkapsner.github.io/CanvasBlocker/test/detectionTest.html
edit: other interesting links about Canvas fingerprinting:
=> shows the summary of canvas fingerprinting scripts found on the homepages of top 100K Alexa sites.
The text was updated successfully, but these errors were encountered: