2020.08.20 update There are still a lot of bugs, so I'll take the time to fix them soon, so please keep updating.
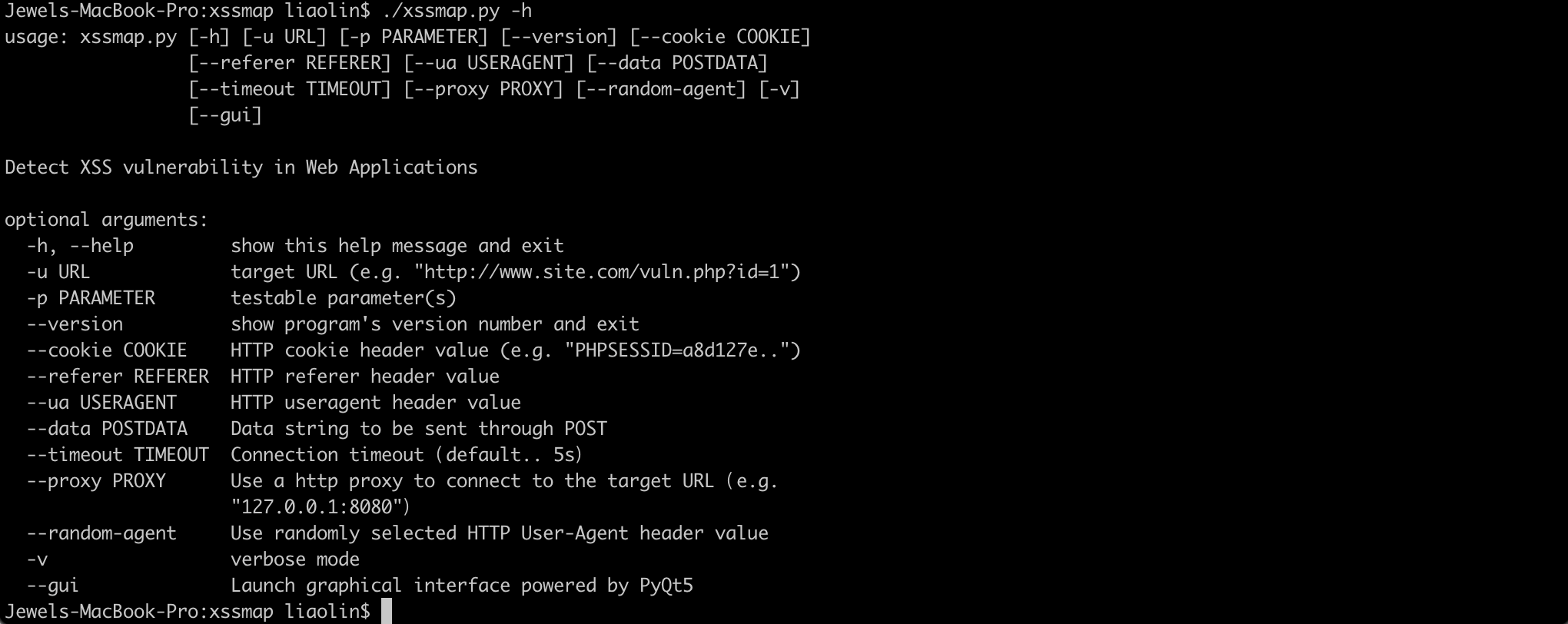
Detect XSS vulnerability in Web Applications
Usage mimics sqlmap, and if you know sqlmap, you can easily handle xssmap!
As simple as below, Just one line of code:
curl -L https://raw.githubusercontent.com/Jewel591/xssmap/master/docs/install.sh|bash
If you get a network error, such as Connection refused, use git clone to install:
git clone -b master https://github.com/Jewel591/xssmap.git
cd xssmap
pip3 install -r requirements.txt
python3.6 xssmap.py -h
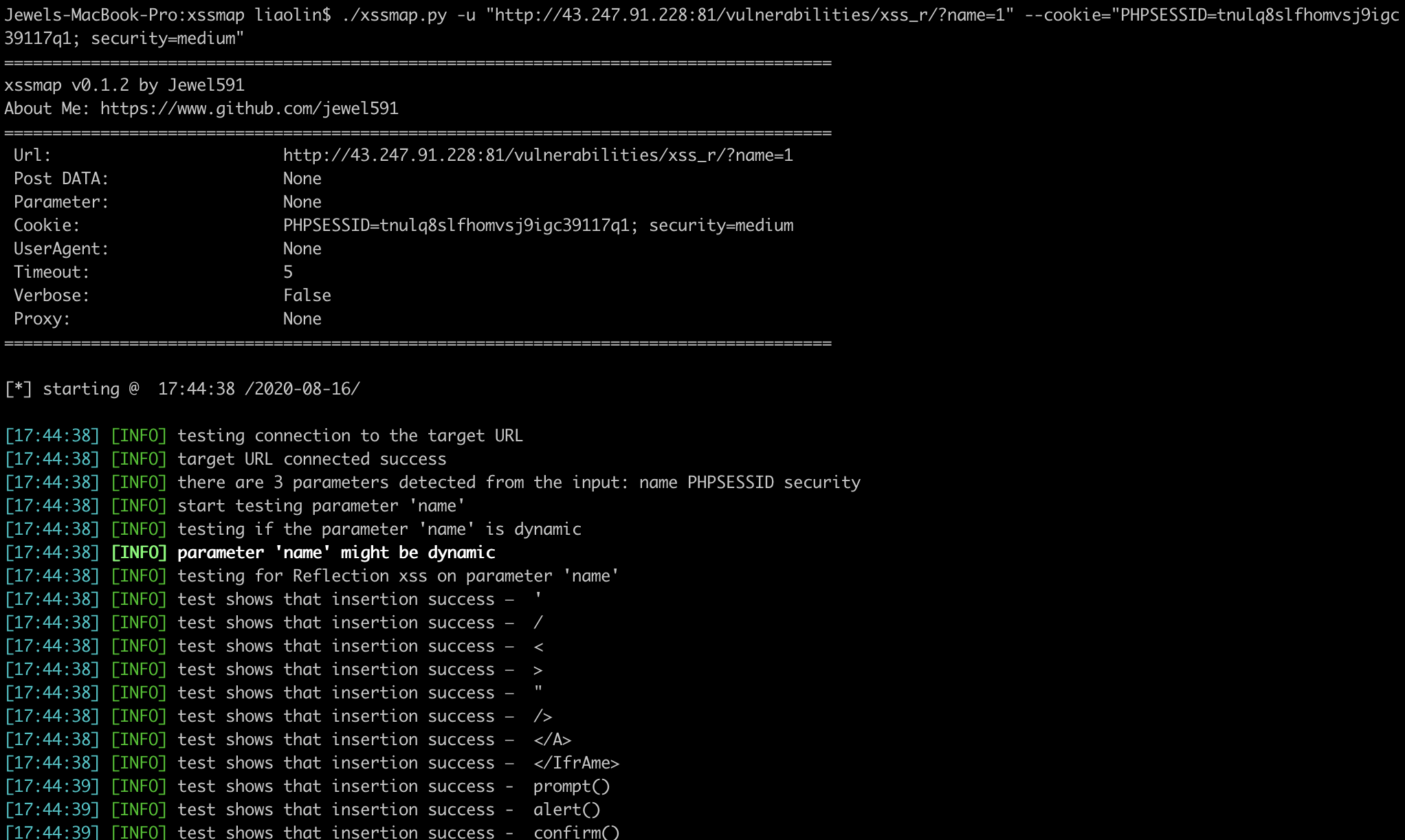
Support POST and GET request methods, support parameter injection detection in cookie, referer, useragent fields For example, test the returnUrl parameter in POST data:
python3.6 xssmap.py -u "https://example.com/login.do" --data="returnUrl=utest" -p returnUrl
- Support url encoding bypass
- Support unicode encoding of HTML tag attribute value to bypass
- Support HTML encoding to bypass the HTML tag attribute value
- Support for flexible replacement of () '"to bypass
- Case bypass
Contributions, issues and feature requests are welcome!
Feel to check issues page
thanks for @dwisiswant0
- DOM XSS Detect
- Json XSS Detect
MIT © Jewel591, Kyle