An entry point to the Cocaine Cloud.
Cocaine HTTP proxy terminates HTTP traffic and transforms it into the binary protocol, allowing to communicate with Cloud services and applications.
It's a high-performance solution, developed to transparently replace the cocaine-tornado-proxy that is written in Python.
The HTTP proxy can now be built only from sources.
You can install a binary compiled with Rust nightly using cargo. Note that this requires you to have Rust nightly with version 1.17 or newer installed.
cargo install --path=PATHAdditionally, if you're a Debian user you may find convenient to build a Debian package using the following command.
cargo install --git=https://github.com/mmstick/cargo-deb
cargo debThe resulted debian package lies in ./target/debian directory.
Backed with Cocaine Framework Rust and MessagePack this HTTP proxy allows to communicate asynchronously with the Cloud applications and services.
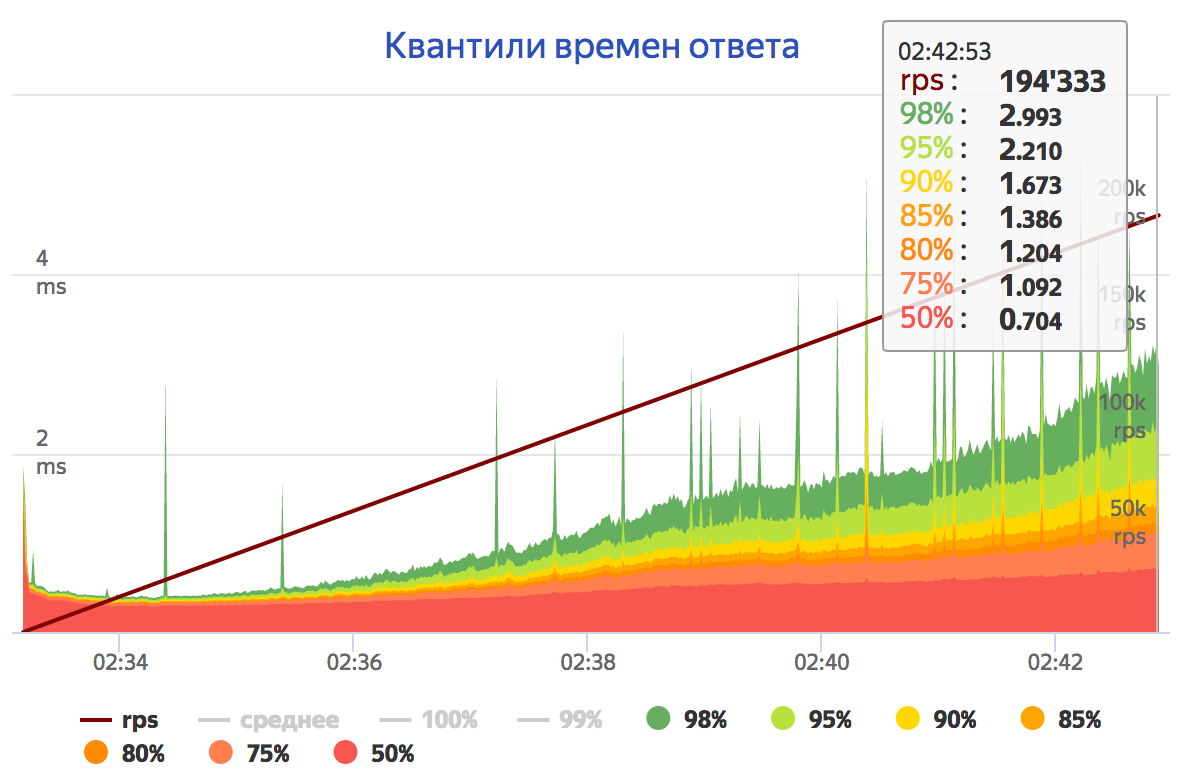
The following load testing results are collected using Yandex Tank, firing proxy that redirects all requests to a Geobase Service.
The proxy runs on a machine with Intel(R) Xeon(R) CPU E5-2660 0 @ 2.20GHz:
The proxy have common and access attribute-based logs and write them directly into the Logging Service completely asynchronously, which allows to route all cluster logs into a single place for further analyze.
The proxy collects various metrics during execution and is able to provide them through monitoring server.
esafronov@local:~$ curl localhost:10000/metrics | python -mjson.tool
{
"connections": {
"accepted": 1681,
"active": 256
},
"requests": {
"count": 57981507,
"m01rate": 227871.29106938263,
"m05rate": 141047.39695553246,
"m15rate": 90542.77725215351
},
"responses": {
"c5xx": {
"count": 188712,
"m01rate": 1.4037895865759178,
"m05rate": 1.4119725792925535,
"m15rate": 1.3532291261984246
}
}
}The proxy is aware of Google Dapper tracing mechanism. Each request is marked with three special internal headers: trace_id, span_id and parent_id, which are transported with it, allowing to build full tracing path to ease debugging.
...
The proxy supports JSON RPC protocol for calling Cocaine services with the following restrictions:
- The "method" parameter must be represented in form of
SERVICE.EVENT. - The "params" parameter may be omitted when a service takes no arguments, an array with positional arguments when a service protocol terminates immediately, named arguments with a fixed format otherwise (see below).
For example let's call "info" method from an "echo" application service (no "params" parameter):
esafronov@local:~$ curl http://localhost:8080/ -H"X-Cocaine-JSON-RPC: 1" -d '{"jsonrpc": "2.0", "method": "echo.info", "id": 0}' | python -m json.tool
{
"error": {
"code": -32001,
"data": "[1]: service is not available",
"message": "Service is not connected"
},
"id": 0,
"jsonrpc": "2.0"
}Calling single-shot event will look like:
esafronov@local:~$ curl http://localhost:8080/ -H"X-Cocaine-JSON-RPC: 1" -d '{"jsonrpc": "2.0", "method": "storage.read", "params": ["collection", "key"], "id": 0}'
{"jsonrpc":"2.0","result":[{"event":"value","value":["Work-work"]}],"id":0}...
...
This project adheres to Semantic Versioning.